GOAD on proxmox - Part5 - VPN access with openvpn
GOAD on proxmox - Part5 - VPN access with openvpn
Now our lab is up and running, but we need to make an easy access on it. Like a lot of ctf with active directory we will create a VPN access to our lab.
To do that we will create an openvpn access with pfsense. A blog post already explain this phase very well and in details : https://www.it-connect.fr/pfsense-configurer-un-vpn-ssl-client-to-site-avec-openvpn/, we will here follow these steps and adapt it to our configuration.
Create openvpn access
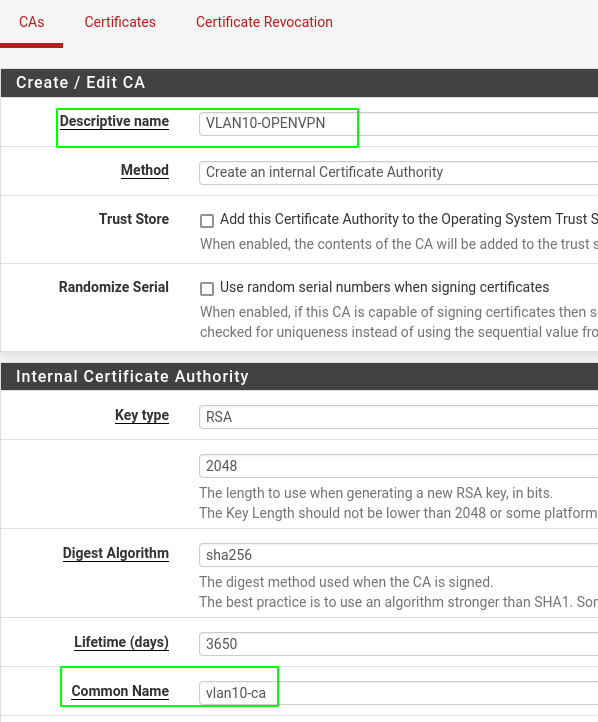
Create certificate autority
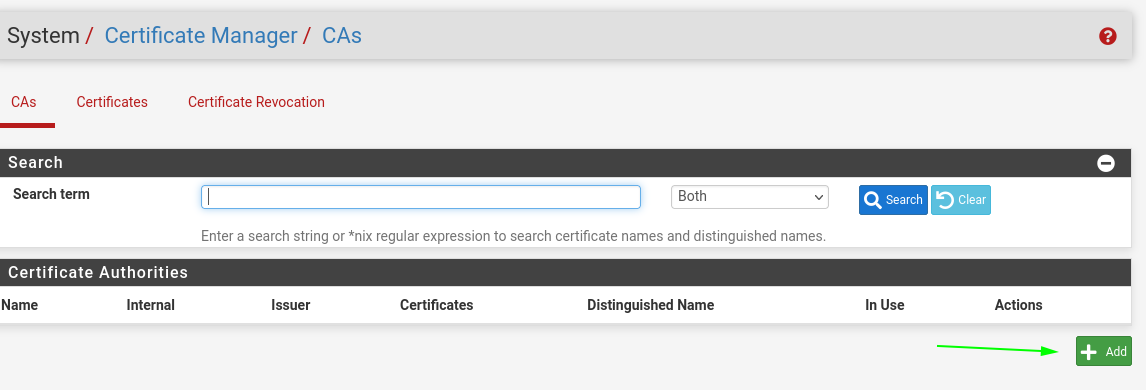
- System > certmanager
- Add an new CAs
- add a name to the ca and create it
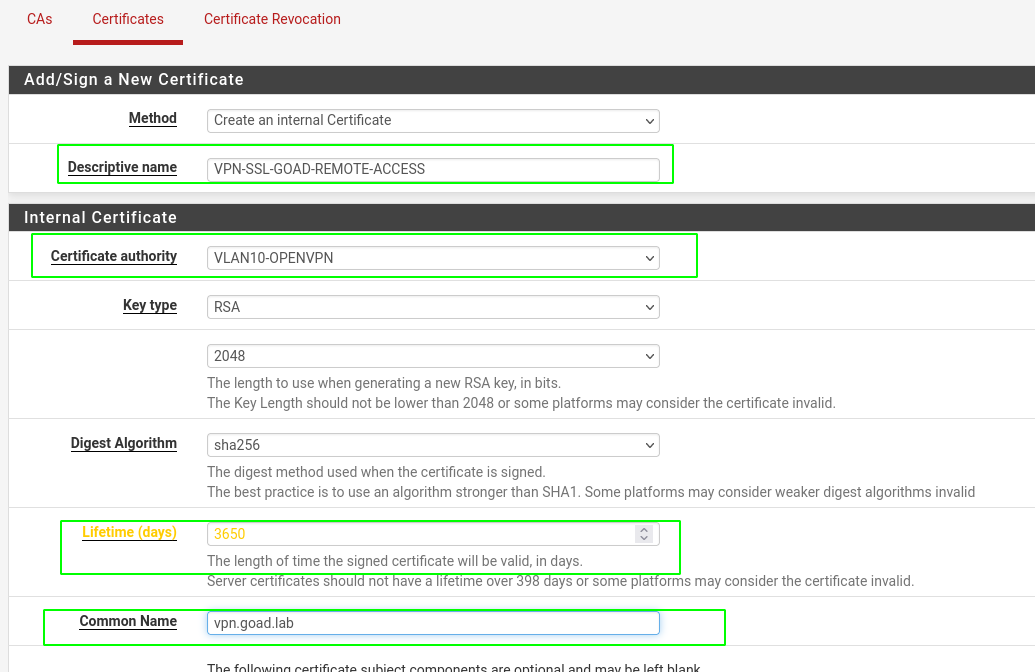
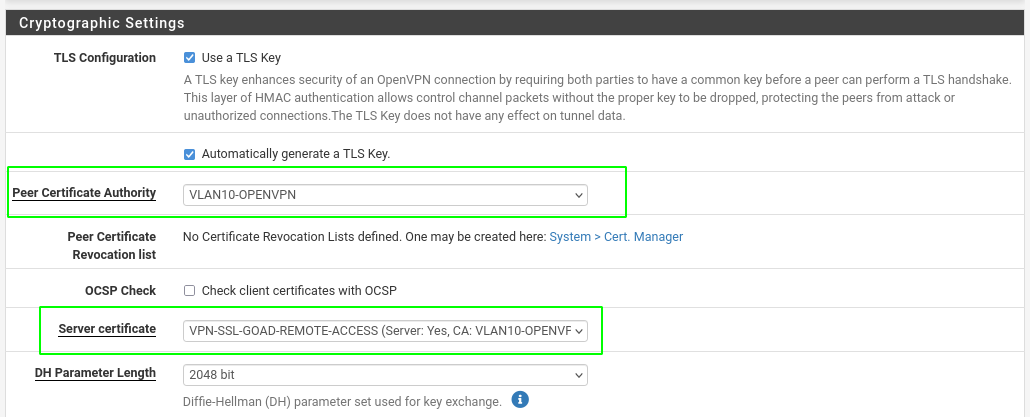
Create certificate server
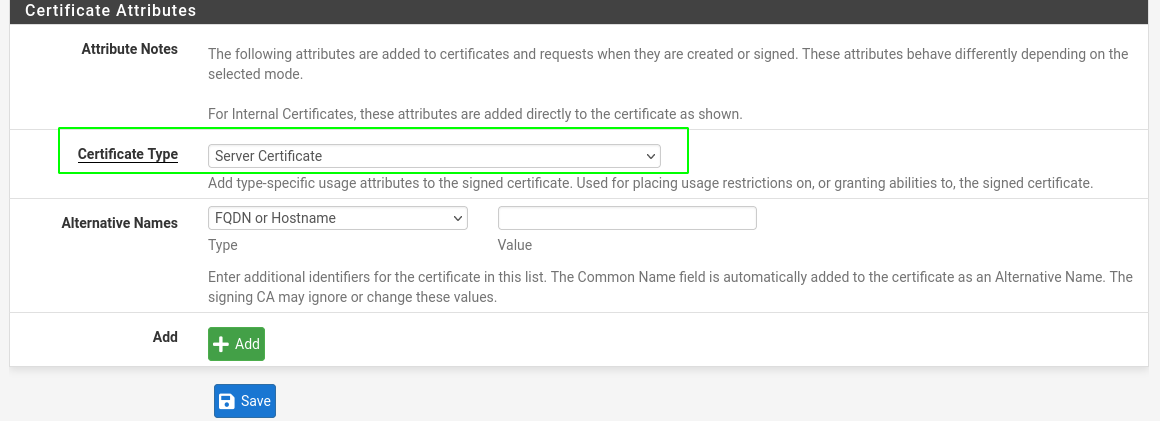
- Create the server certificate, set the certificate authority created before, a descriptive name, a common name like “vpn.goad.lab”, a lifetime duration and a certificate type “server certificate”
- And save it
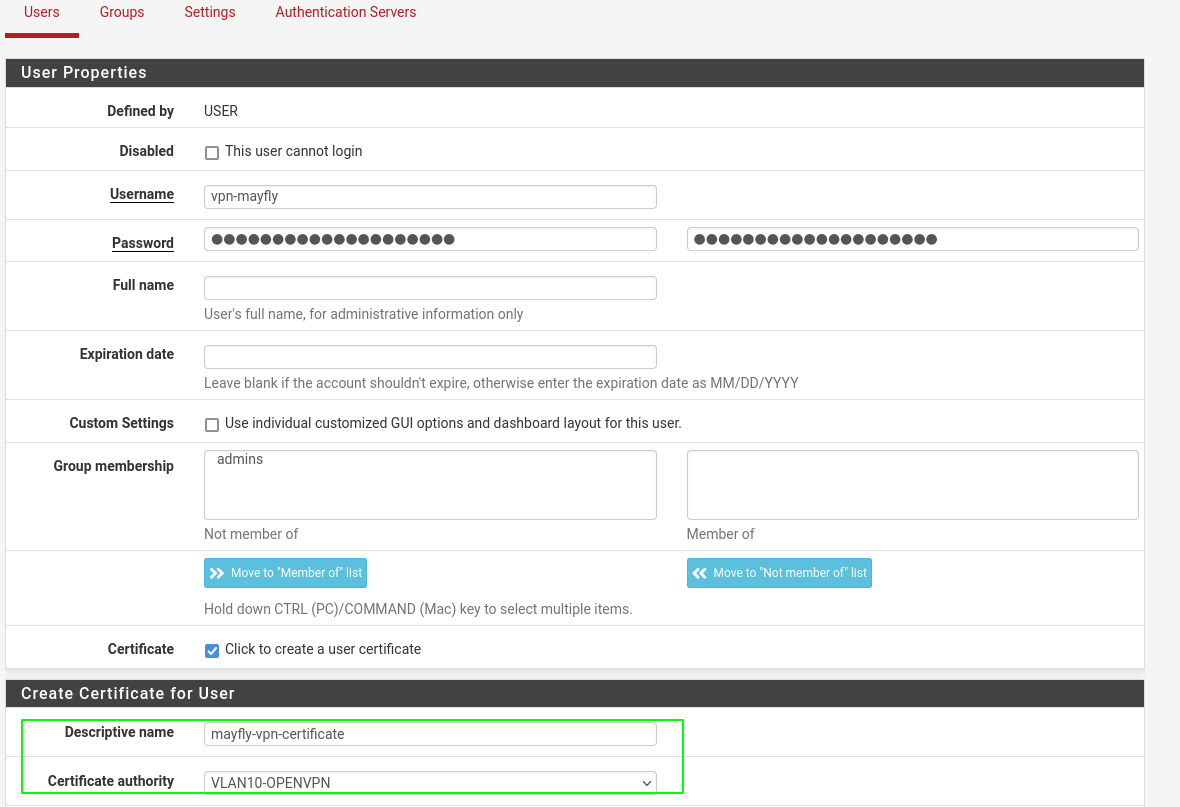
Create local user
- In order to use the vpn we will create local users
- Go to System > User manager > user
- Create a non login user with a certificate attached to the certificate authority
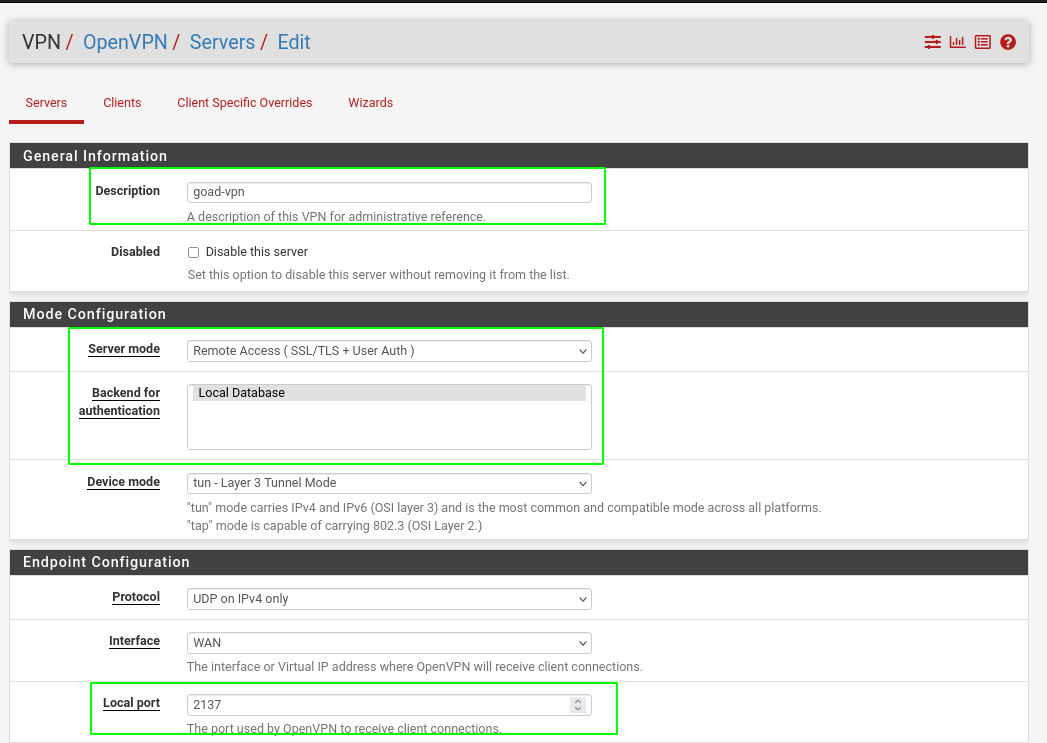
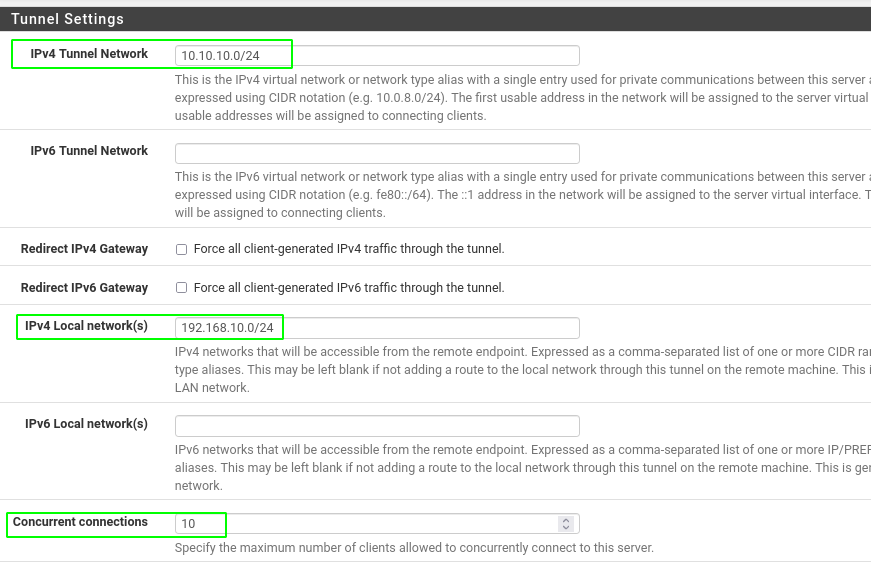
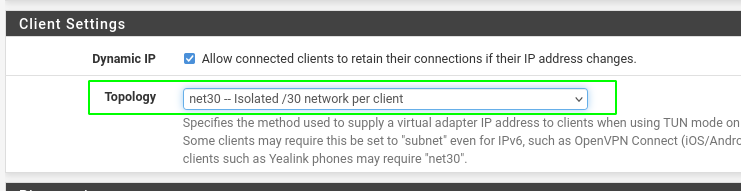
Create open vpn service
- Got to VPN > openVPN
- Add a new server
Add package openvpn client export
System > Package Manager > Available Packages 
- Install the package
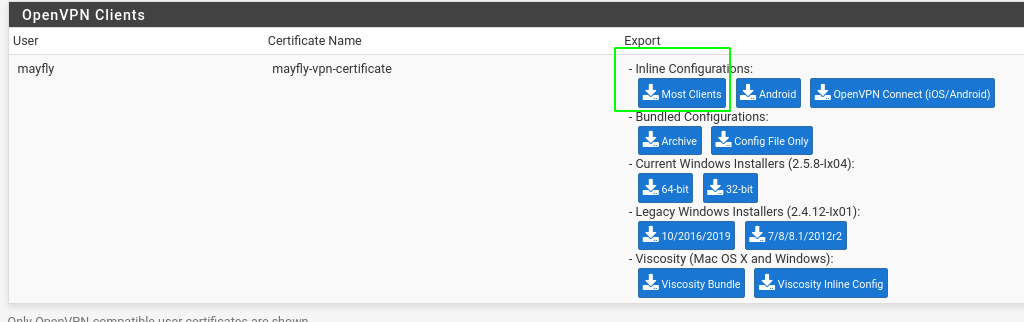
- Now got to VPN > OpenVPN > client export
- And export the certificate
Download and use certificate
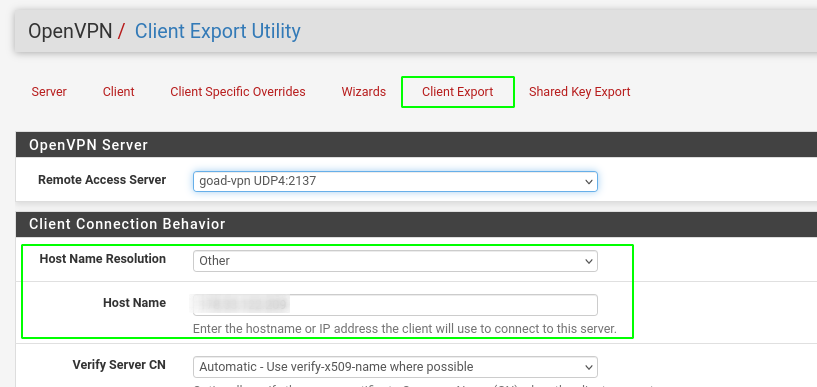
Now go to VPN > openvpn > client export
Change the host name resolution to other :
- In the bottom of the page you can download your vpn configuration
Configure firewall
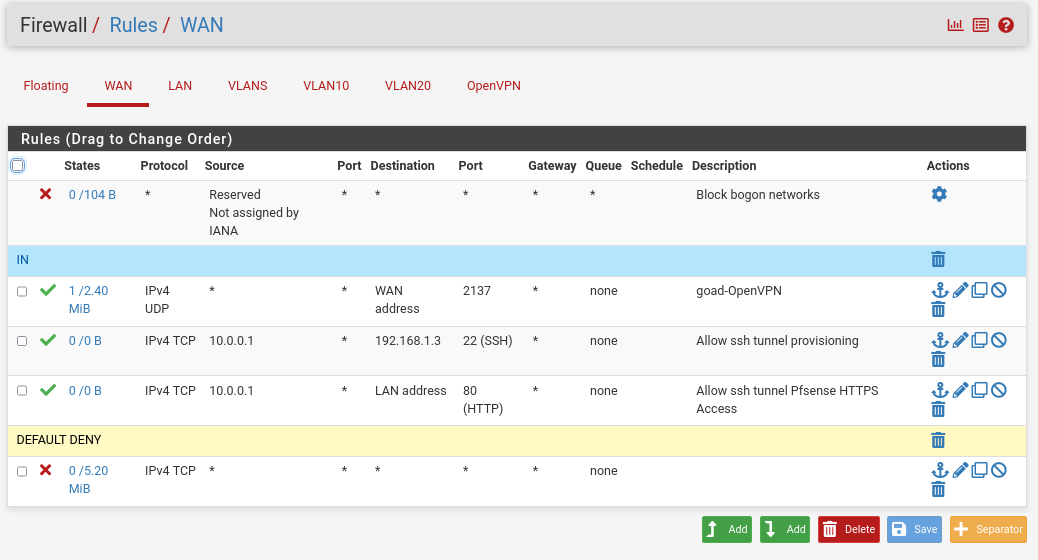
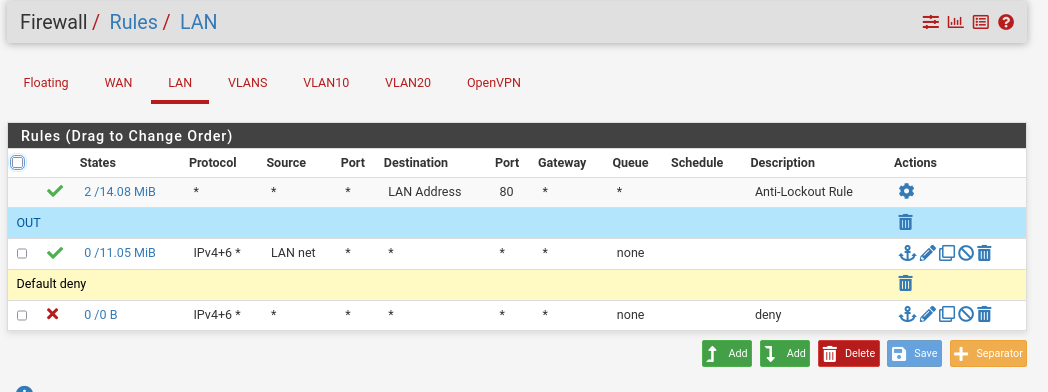
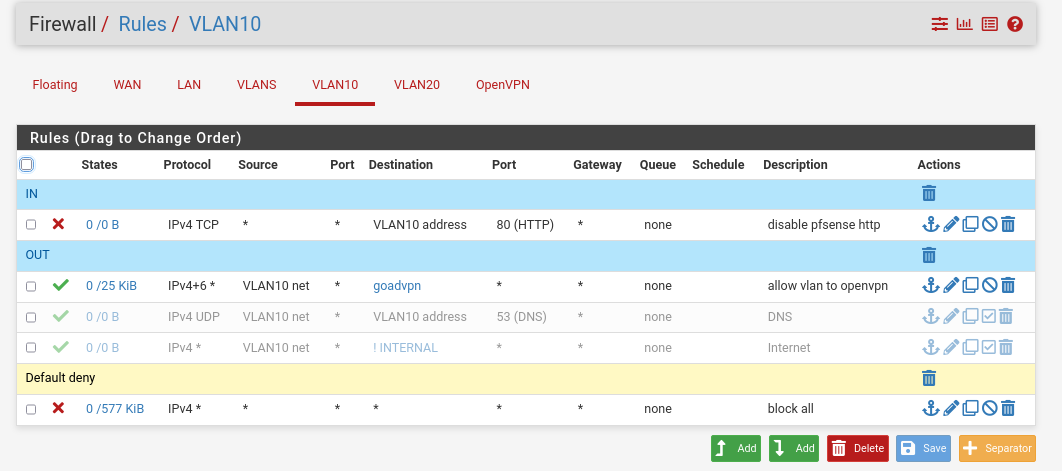
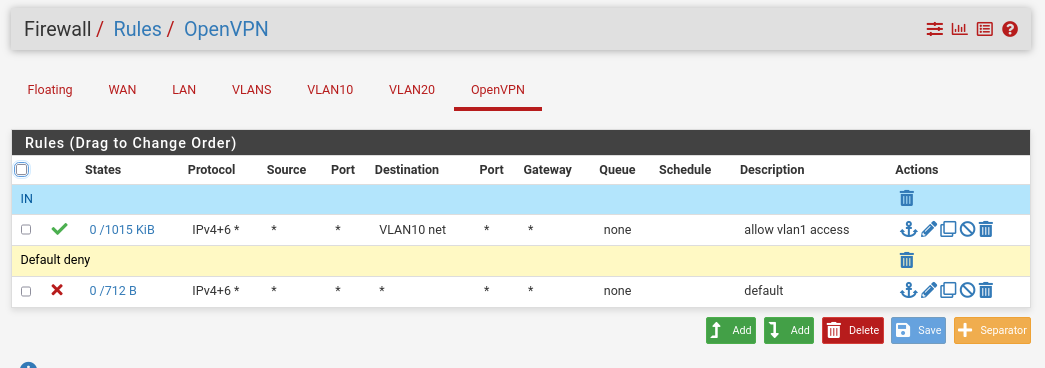
Now we will review the firewall rules :
WAN
- LAN
- VLAN
- OPENVPN
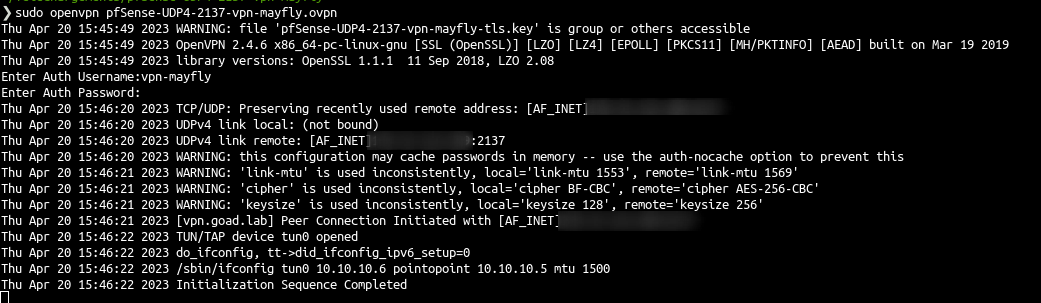
Connect
- And now you could connect to the VPN and enjoy :)
- And now you can use it as your lab !
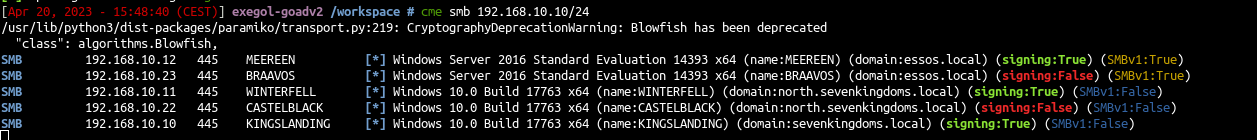
- If you want to listen for responder you can also add a CT in the vlan10 to listen LLMNR request.
resources
FR:
EN:
This post is licensed under CC BY 4.0 by the author.